Verify every device,
secure any user.
Ensure your team stays productive and keep your data secure
—while preserving privacy and requiring minimal effort.Securing devices for leading organizations like

Privacy first, respectful of ownership. XFA secures BYOD, managed, and external devices with a lightweight layer that never crosses the line.
Give freedom, keep security. Let people work on any device they want with a smooth experience that boosts productivity, happiness and offers protection.
Learn how to protect BYOD & Freelance devicesXFA has an user-friendly and straightforward process for onboarding people. Additionally, I value that it supports a bring-your-own-device policy, unlike many other tools out there, which are both costly and restrictive.

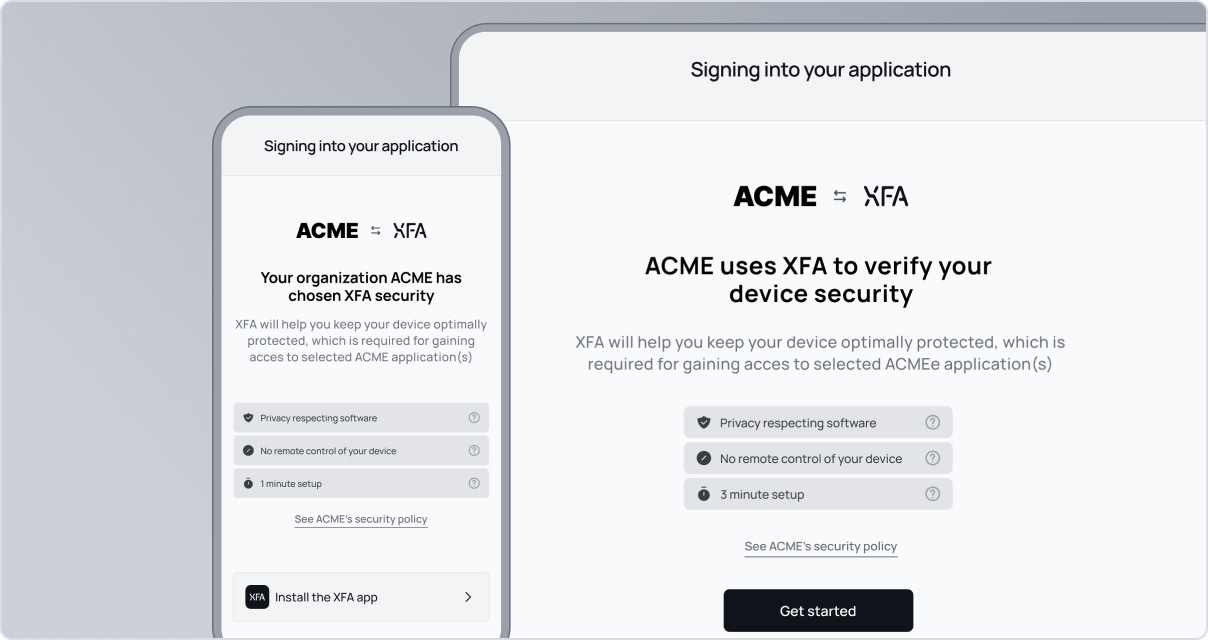
Security on autopilot. XFA gives the visibility you need without taking over devices. Easy setup for you and your team. Device verification at login without IT overhead.
SCALABILITY
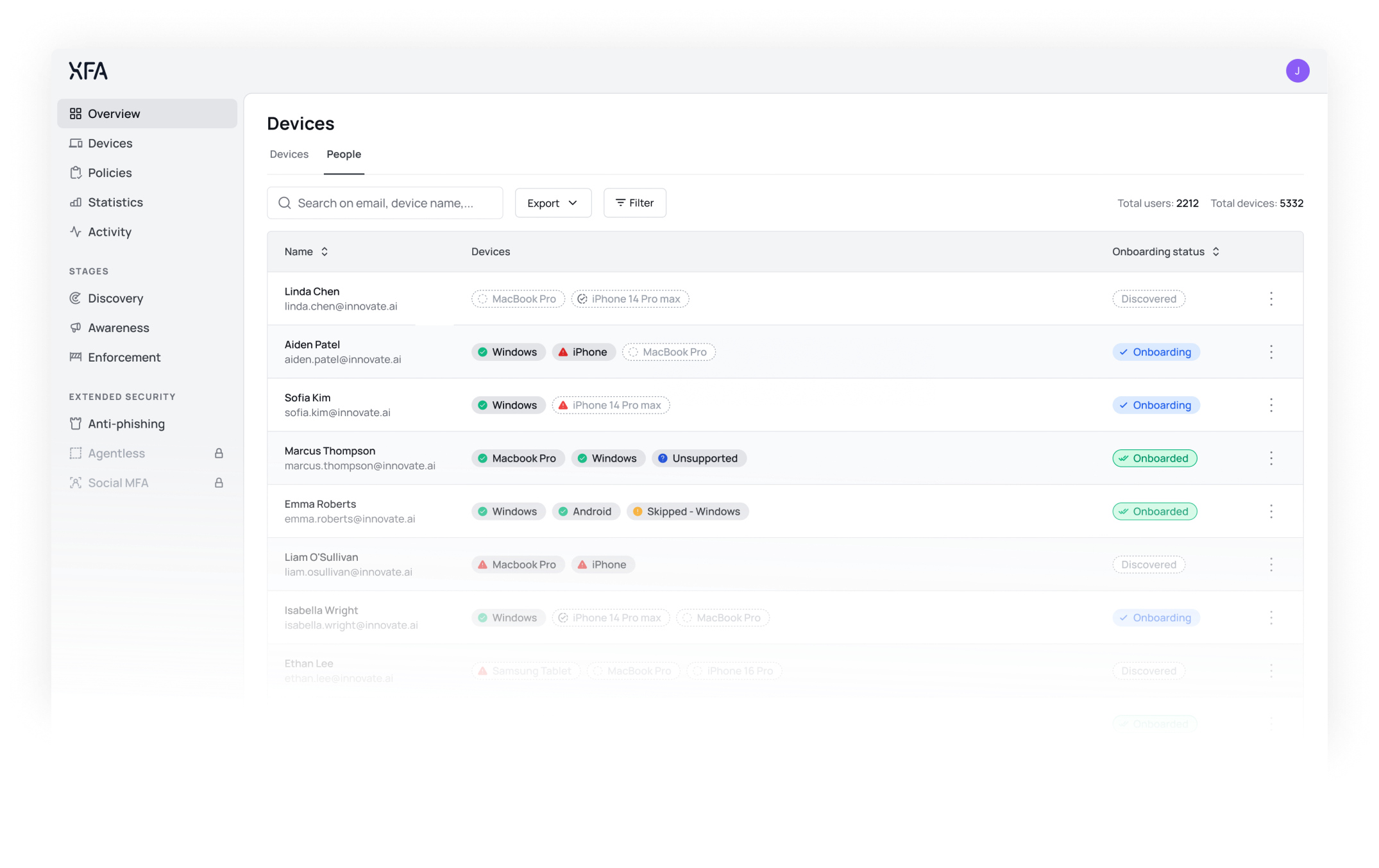
Quick and easy self-onboarding for your entire team with confidence
ZERO TRUST
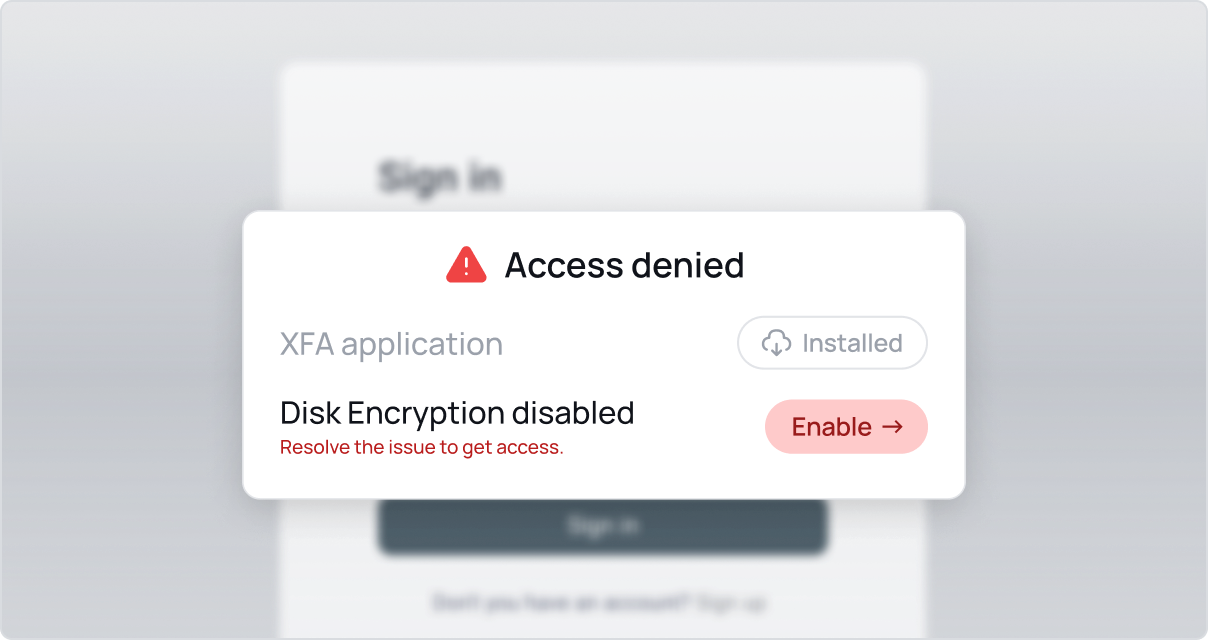
Only allow secure devices to access your business data
Discover every device used for work. From BYOD to fully managed, get complete visibility and the evidence you need for compliance certifications.
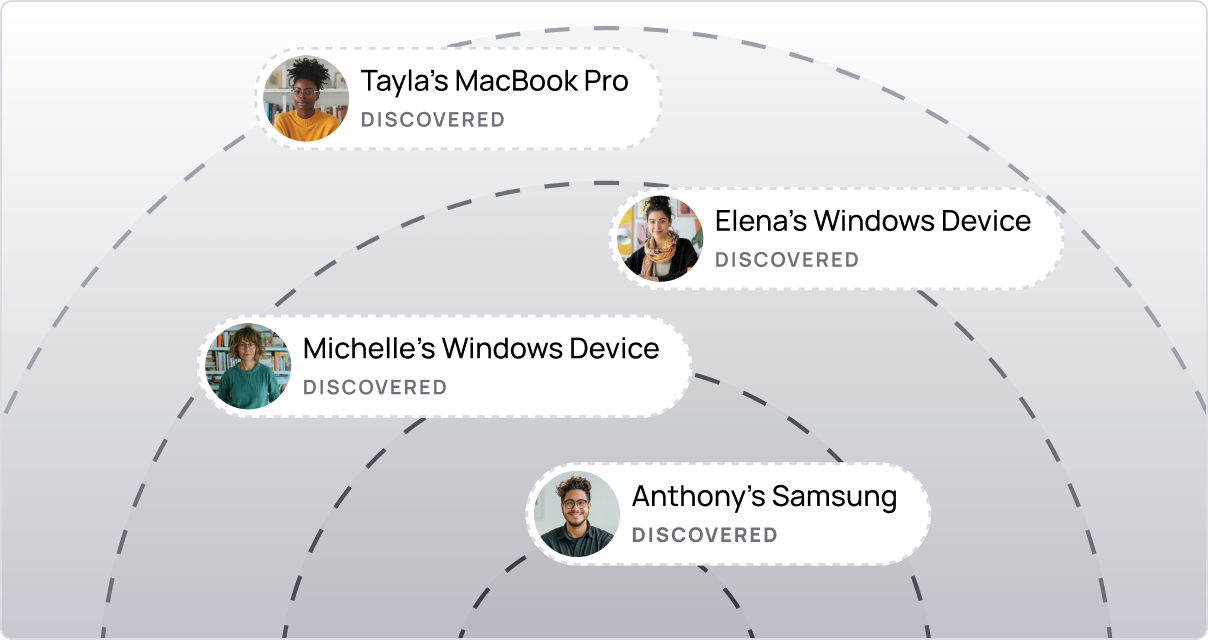
DISCOVERY
Discover every device accessing your platforms. In just minutes

COMPLIANCE
Share your compliance status with platforms such as Vanta, Drata, Trustcloud and Thoropass.
See all devices.
Raise security awareness.
Enforce protection.
In just minutes.
We integrate with your Identity Provider, discover all connected devices, check their security, and enforce compliance-ready access controls.
What our customers say
“XFA is crucial for us, as we rely on both managed and unmanaged devices. XFA's discovery phase helps us identify what devices are accessing sensitive information and ensures they comply with our security policies.”
Read the full testimonial →No time for a meeting?
Watch our solution video now.

We'd love to show you our solution and how:
- Every device is discovered automatically.
- Security is enforced without taking control or ownership of the device.
- Users can verify their devices from anywhere, in seconds.





