Address the gaps in your device security
From managed to unknown devices, uncover all connections to your business. Protect sensitive data and close the security gaps that leave your organization exposed.
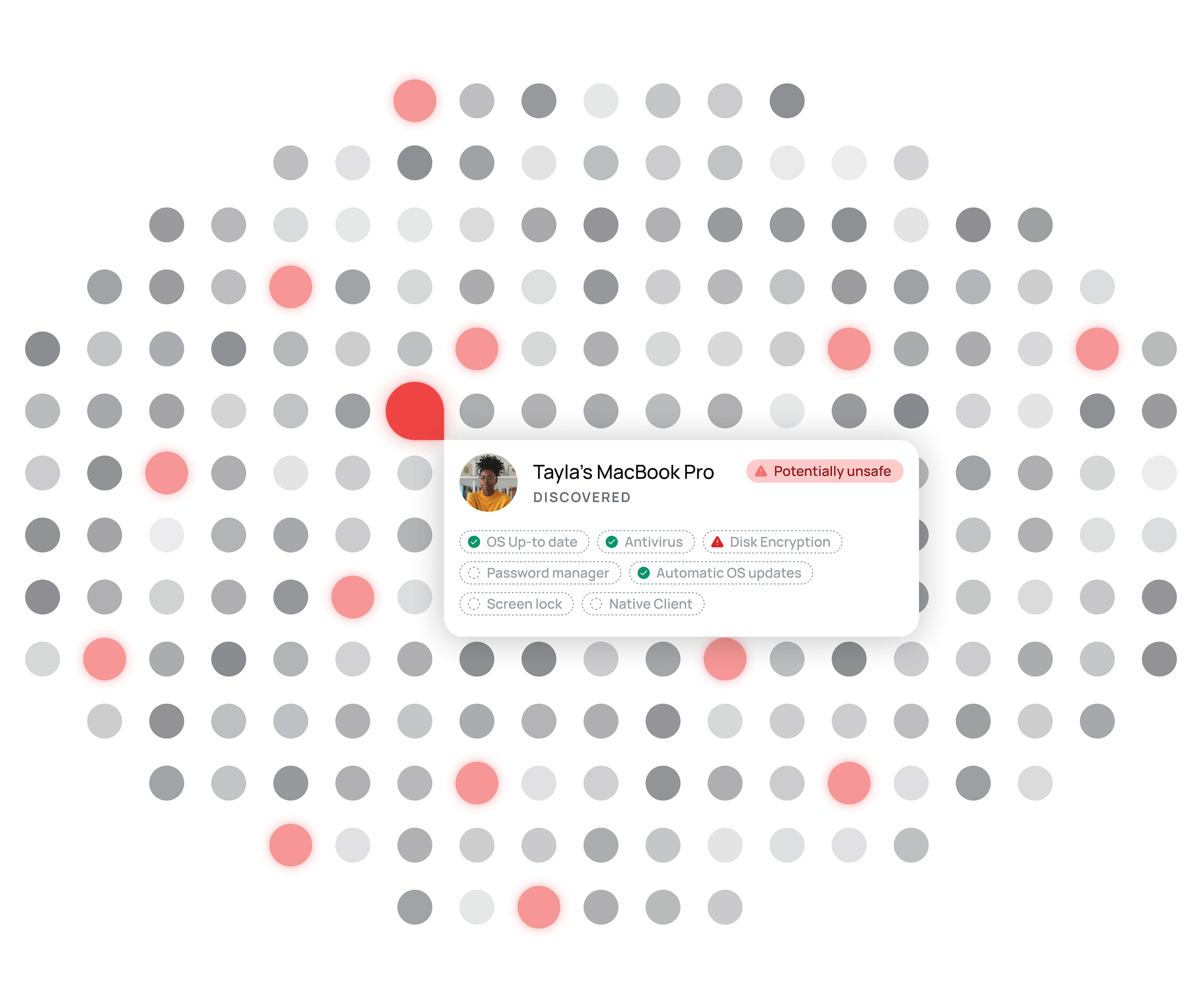

Security doesn't have to be complex. XFA fills gaps in device security with automated protection, covering every device, managed or unmanaged. Simplify security and keep your team focused on what matters.
Why XFA?
Security that works for every device.
Accept the risk
Your current MDM can't cover everything. You might write a policy, hope employees follow it, and accept the risk. But hope isn't a strategy, and unknown devices remain a ticking time bomb.
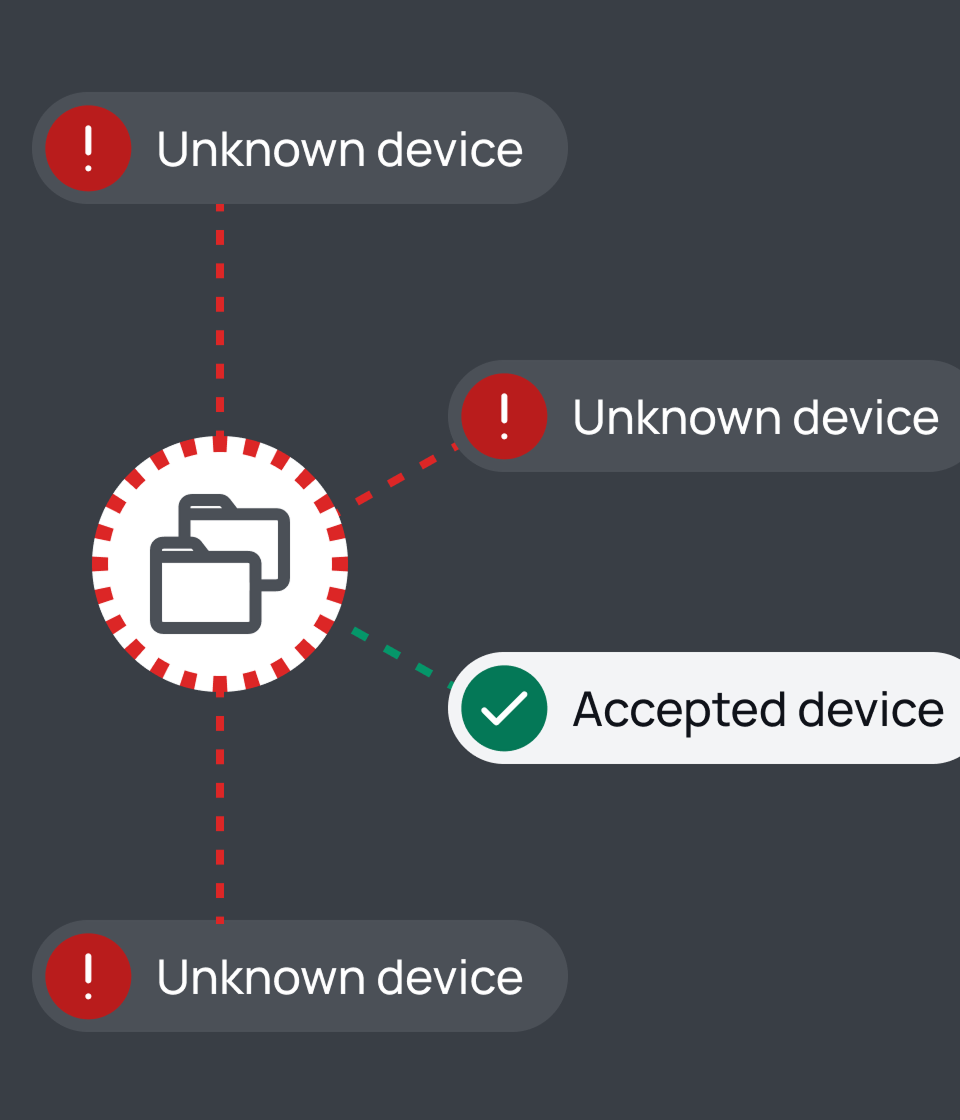
Enforce restrictive access controls
Block all unmanaged devices entirely. While this reduces some risks, it creates operational chaos. Executives demand exceptions, contractors can't work efficiently, and productivity suffers.
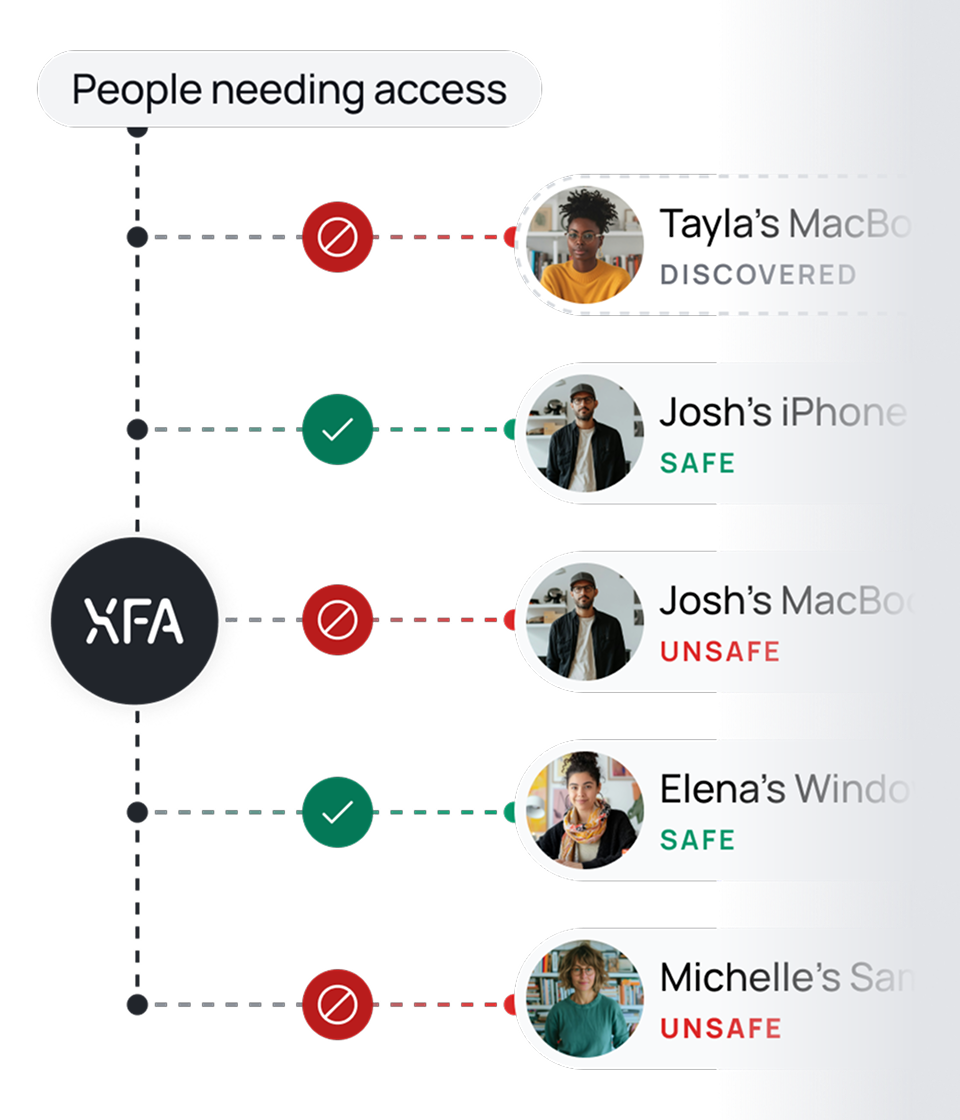
Use XFA to cover all devices
XFA secures every device. Managed or unmanaged. Only safe devices access your platforms, eliminating blind spots. With XFA, you know every device accessing your systems and ensure they're secure.
Close the gaps.
Stop unknown devices from becoming your weakest link.
Partial security setups and traditional MDMs often leave critical gaps. XFA ensures that no device slips through unnoticed, providing full coverage inside and outside MDMs. With real-time risk insights, seamless integration, and automated controls, your organization stays one step ahead of vulnerabilities.
Shine a light on security gaps
Identify security gaps overlooked by conventional solutions. XFA provides complete visibility into devices inside and outside of your ecosystem.
Access for secure devices, block the rest
Ensure adherence to your security standards. Unsafe devices are blocked, guaranteeing every device accessing your systems is secure, MDM or not.
Plug into your current infrastructure
Easily incorporate XFA into your existing infrastructure. With minimal setup time, XFA adapts to your workflows and safeguards you've put into place.
The reality of modern work
See why the "old way" of managing devices is failing. A look at the challenges of the hybrid workforce (and why we need a new approach).
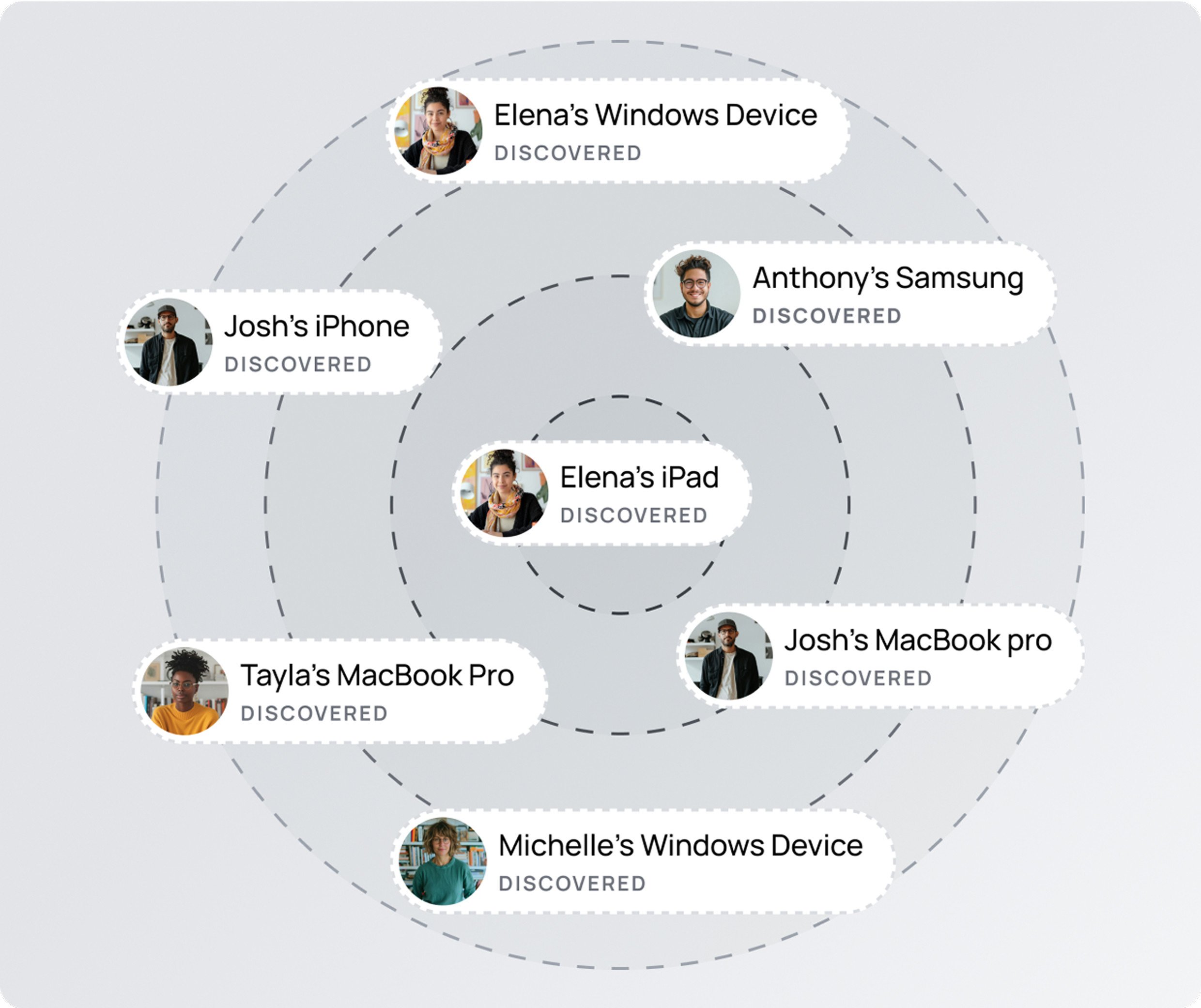
Discover every device.
No matter where it hides.
Get complete visibility into all devices accessing your business platforms, whether managed, unmanaged, or unknown. XFA continuously discovers devices in the background and identifies every connection to your network.
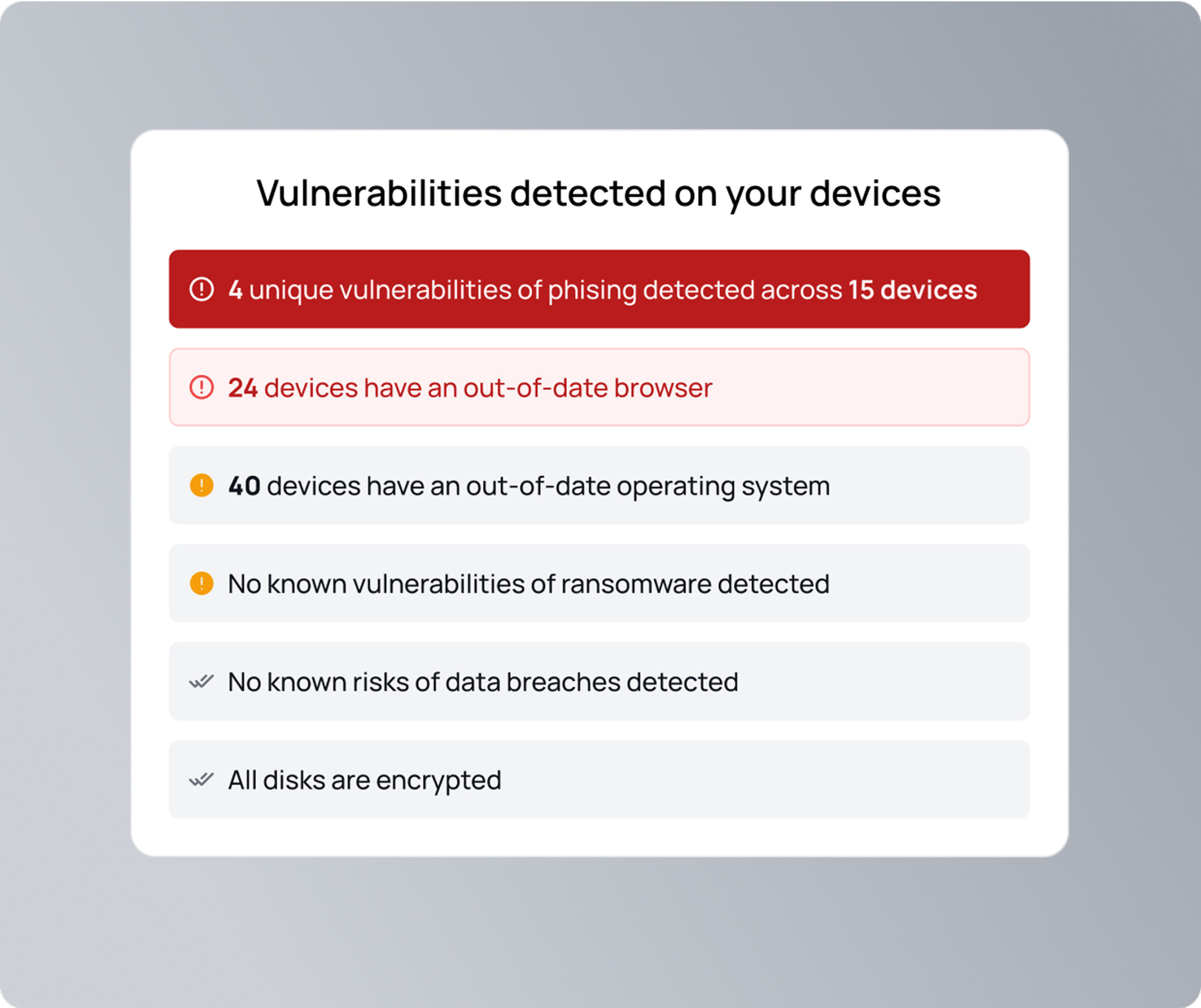
Spot vulnerabilities before they become threats.
Identify security risks the moment they appear. With clear categories like data breaches, ransomware, and phishing, you'll see which devices are affected. Immediate alerts help you act fast and prevent threats from escalating.
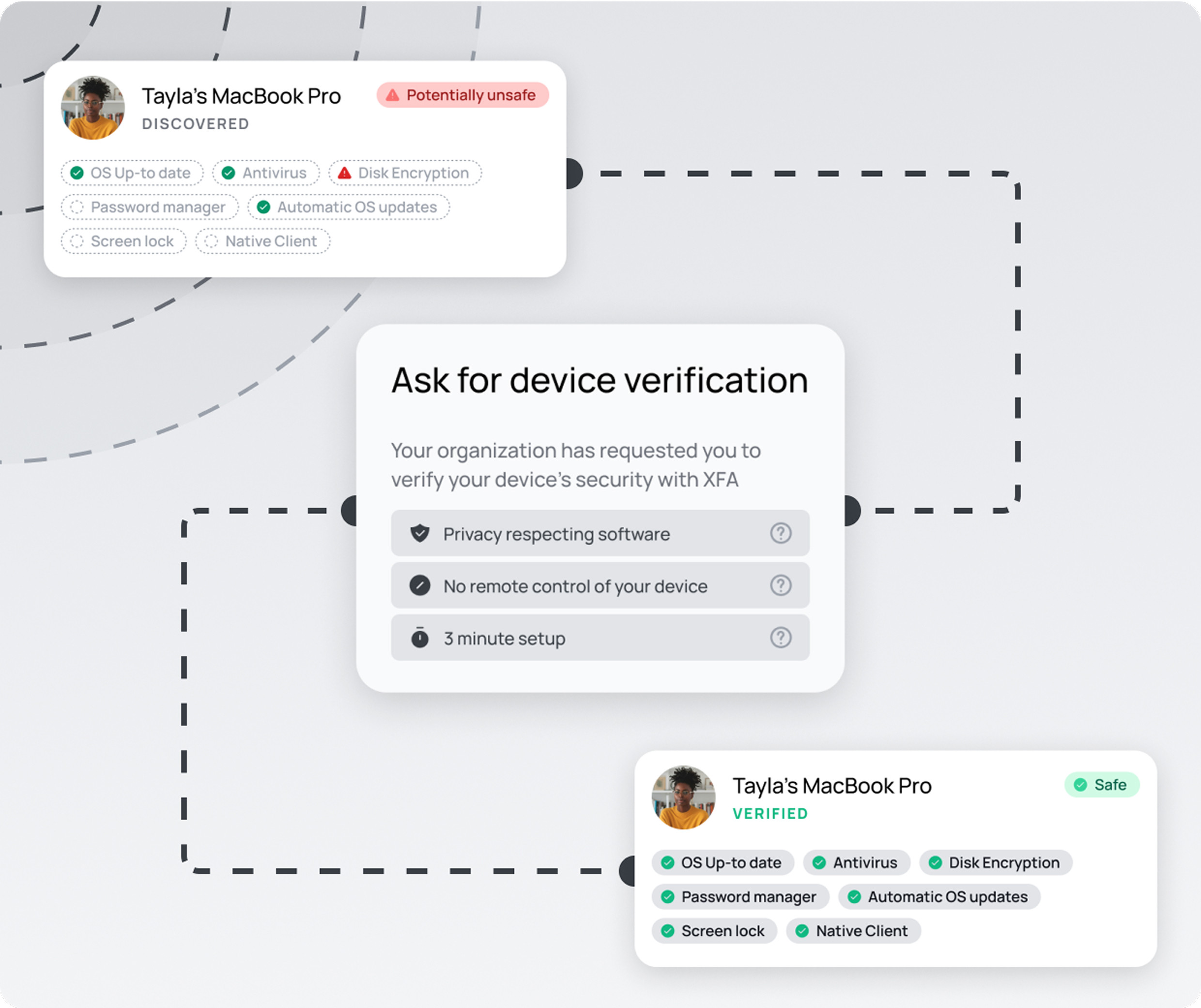
Verify every device.
Only allow the secure.
Enforce Zero Trust access by controlling which devices can connect to your business applications. XFA acts as an extra authentication factor, checking device security measures like OS updates, disk encryption, and antivirus status during sign-in to ensure only trusted devices get access.
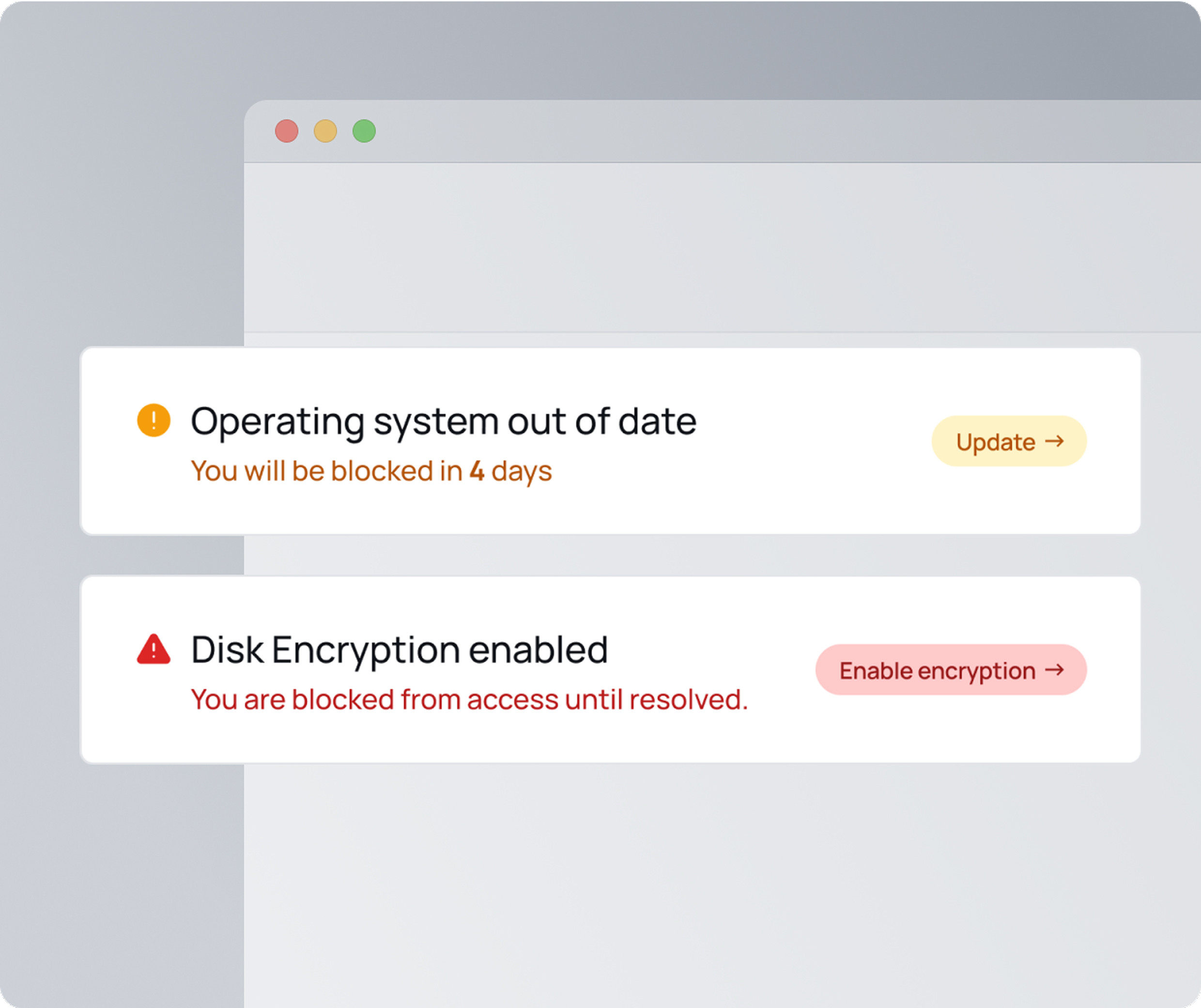
Security that guides.
So no one gets blocked.
Getting blocked slows work down. XFA gives users clear steps to fix security issues themselves, so they can regain access without IT intervention. Simple guidance, fewer disruptions, and a safer business.
XFA is crucial for us, as we rely on both managed and unmanaged devices. XFA's discovery phase helps us identify what devices are accessing sensitive information and ensures they comply with our security policies.
All devices protected.
Even those you don't know about.
Proactively eliminate vulnerabilities
With real-time monitoring and automated updates, XFA uses CVEs to map and address security threats across all devices, ensuring risks are identified and resolved before they impact your business.
Know every device, control access.
XFA ensures every device is accounted for, including those outside your MDM. Only compliant devices gain access, while untrusted ones are automatically blocked. Security is seamless and reliable.
Security that manages itself.
Onboarding devices happens seamless and automatic. Unsafe devices are blocked instantly. Your IT team focuses on innovation while XFA ensures device security in the background.
Questions?
We've got answers.
XFA discovers and identifies all devices accessing your business platforms, detecting security risks such as outdated software, missing encryption, and non-compliant security settings. It integrates with identity providers to enforce access policies, ensuring only secure devices can connect. The XFA application verifies device security and provides clear remediation steps. Non-compliant devices are blocked until security requirements are met, preventing breaches and maintaining compliance.
Traditional MDM solutions take full control of every device to ensure security, which can be costly, difficult to scale, and lacks the flexibility needed for a modern workforce. XFA provides a modern alternative by continuously discovering all devices accessing your business platforms, including managed, personal, and contractor devices. Instead of enforcing rigid controls, XFA verifies each device's security status based on your policies and identifies risks such as outdated software, missing encryption, or non-compliant settings. If a device does not meet security requirements, XFA alerts administrators and guides users through clear remediation steps before granting access.
XFA continuously analyzes authentication logs from identity providers to discover all devices, including managed and unmanaged ones. To verify their security compliance, users install the XFA application on their devices without granting admin permissions. This ensures organizations can enforce security policies while maintaining user privacy, as only the device's security status is shared.
XFA can be deployed in minutes. Once connected to your identity provider, it automatically starts discovering devices, giving you instant visibility into all devices accessing your business platforms. From the next sign-in session, employees are guided through a quick three-minute self-onboarding process to install the XFA application on their devices without requiring admin permissions. This ensures devices are verified for security compliance with minimal effort from IT. Need extra help deploying XFA? We offer three months of dedicated onboarding support as an optional add-on. Talk to sales →
XFA can detect a wide range of security risks, including outdated operating systems, disabled disk encryption, missing or installed password managers, and outdated browsers, among others. Additionally, XFA maps these security checks to known Common Vulnerabilities and Exposures (CVEs), helping organizations identify and address potential threats before they become a risk.
XFA secures BYOD devices by enforcing security policies at the identity level rather than taking full control of the device. Employees can continue using their personal devices while ensuring they meet security standards such as encryption, OS updates, and browser security settings. If a device does not comply, XFA blocks access and guides users through remediation steps before granting access. This ensures security without compromising privacy.
Yes, but only when device security verification is needed. Employees install the lightweight XFA application on their desktop or mobile device to confirm compliance with security standards, without granting admin permissions or full device control. XFA only checks whether essential security features, such as software updates are done and disk encryption is enabled. This ensures strong security and compliance while maintaining user privacy.
Want to close your device security gaps?
Let's talk.




