Secure every device.
Freelancers and employees using personal devices create security blind spots. XFA ensures only secure devices can access your business, without disrupting workflows or complicating management.


Freelancers and BYOD users need access, but you need security.
XFA makes it easy to enforce device protection without intrusive control or complex IT setups.
Why XFA?
Security that adapts to your people.
Do nothing, hope for the best
Choosing not to secure devices means relying solely on trust and hope. No controls, no monitoring, no way to know if an unprotected device is putting business data at risk. Until it's too late.

Legal agreements don't stop threats
Skip device security and rely on written policies. People secure their own devices and try to follow the rules. But policies aren't protection, and one unsecure device could endanger your business.

Use XFA for secure access
XFA protects business data while keeping devices secure. Employees onboard easily without giving admin rights to their device, ensuring privacy and uninterrupted work.
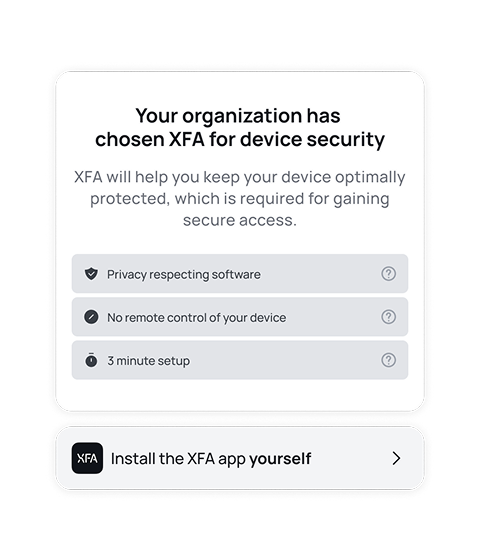
No device left behind.
Consistent protection for every device.
Security should adapt to how your team works, not the other way around. XFA ensures every device meets security standards without adding complexity. With real-time risk insights, seamless onboarding, and compliance-ready controls, your business stays protected while employees work freely and securely.
See every device at a glance
Automatically detect and assess every device accessing your business systems, whether company-owned or personal.
Security and compliance without overreach
Verify compliance and vulnerabilities without invading privacy. XFA checks security status while respecting personal device boundaries.
Plug into your current infrastructure
Easily incorporate XFA into your existing infrastructure. With minimal setup time, XFA adapts to your workflows and safeguards you've put into place.
The reality of modern work
See why the "old way" of managing devices is failing. A look at the challenges of the hybrid workforce (and why we need a new approach).
Every device accounted for.
Every risk monitored.
XFA Discovery continuously monitors both existing and new devices in real time. Get instant insights into security risks and automatically block unsafe devices or prompt users to update before granting access.
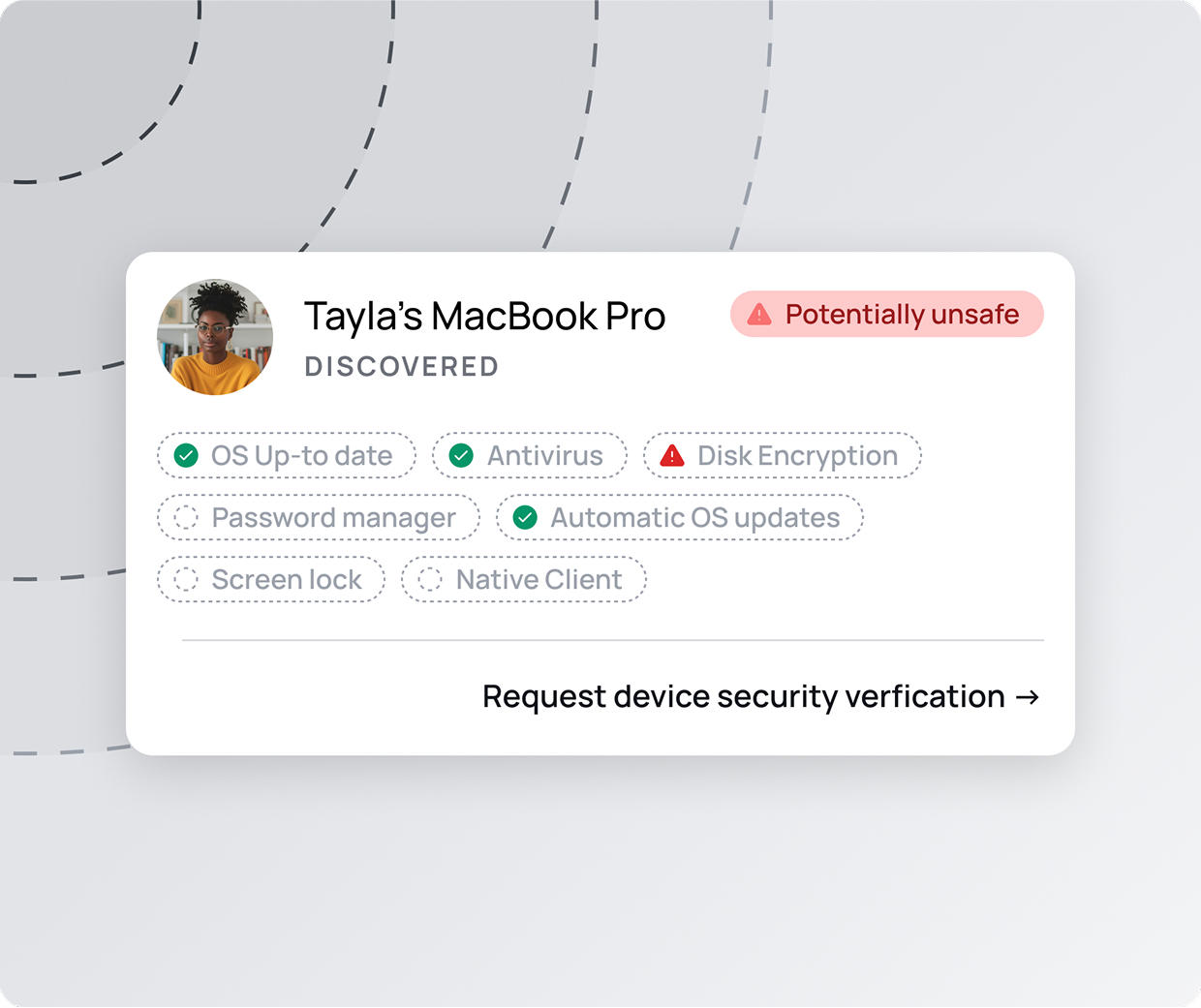
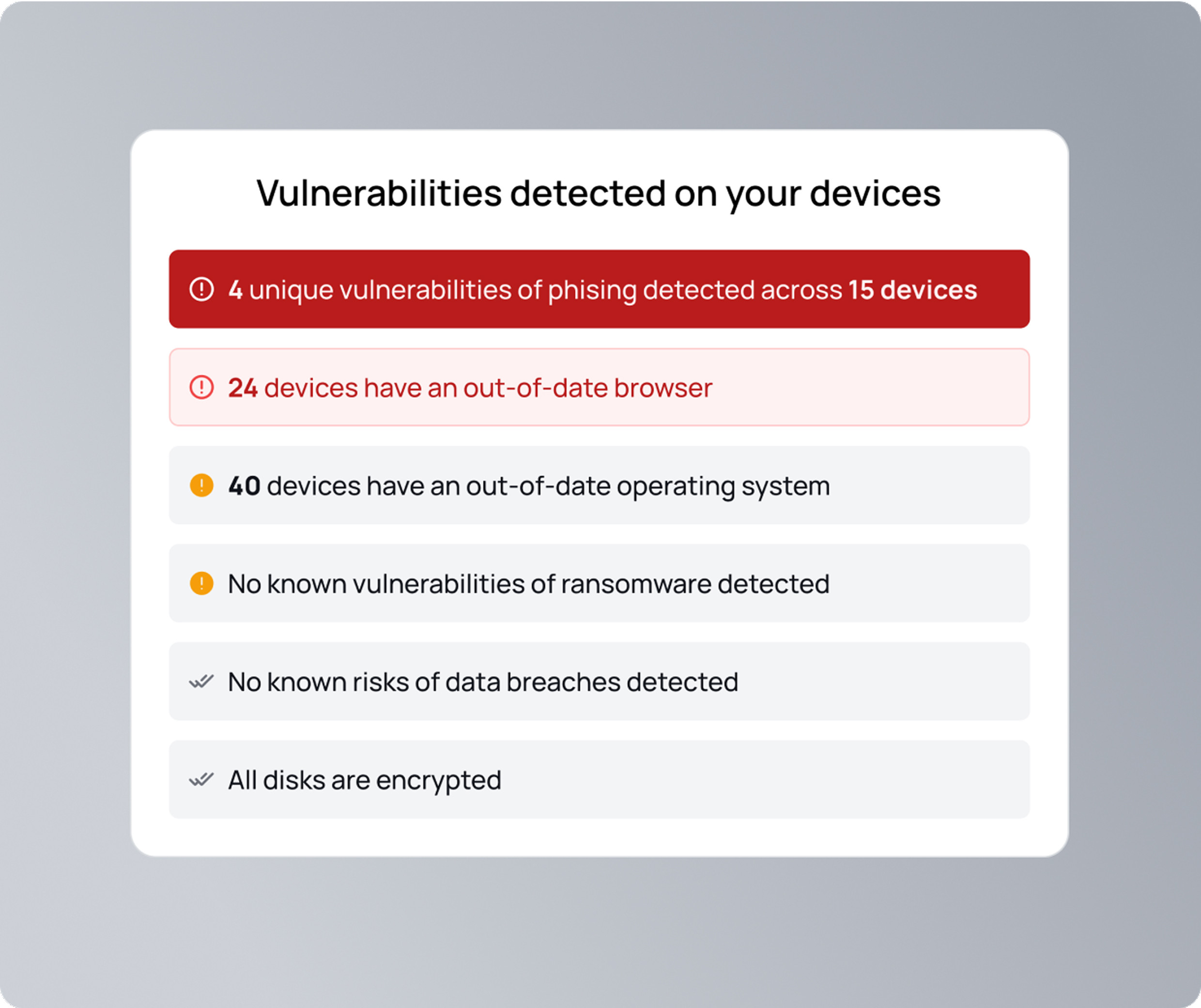
Spot vulnerabilities before they become threats.
Identify security risks the moment they appear. With clear categories like data breaches, ransomware, and phishing, you'll see which devices are affected. Immediate alerts help you act fast and prevent threats from escalating.
Verify every device.
Only allow the secure.
Enforce Zero Trust access by controlling which devices can connect to your business applications. XFA acts as an extra authentication factor, checking device security measures like OS updates, disk encryption, and antivirus status during sign-in to ensure only trusted devices get access.
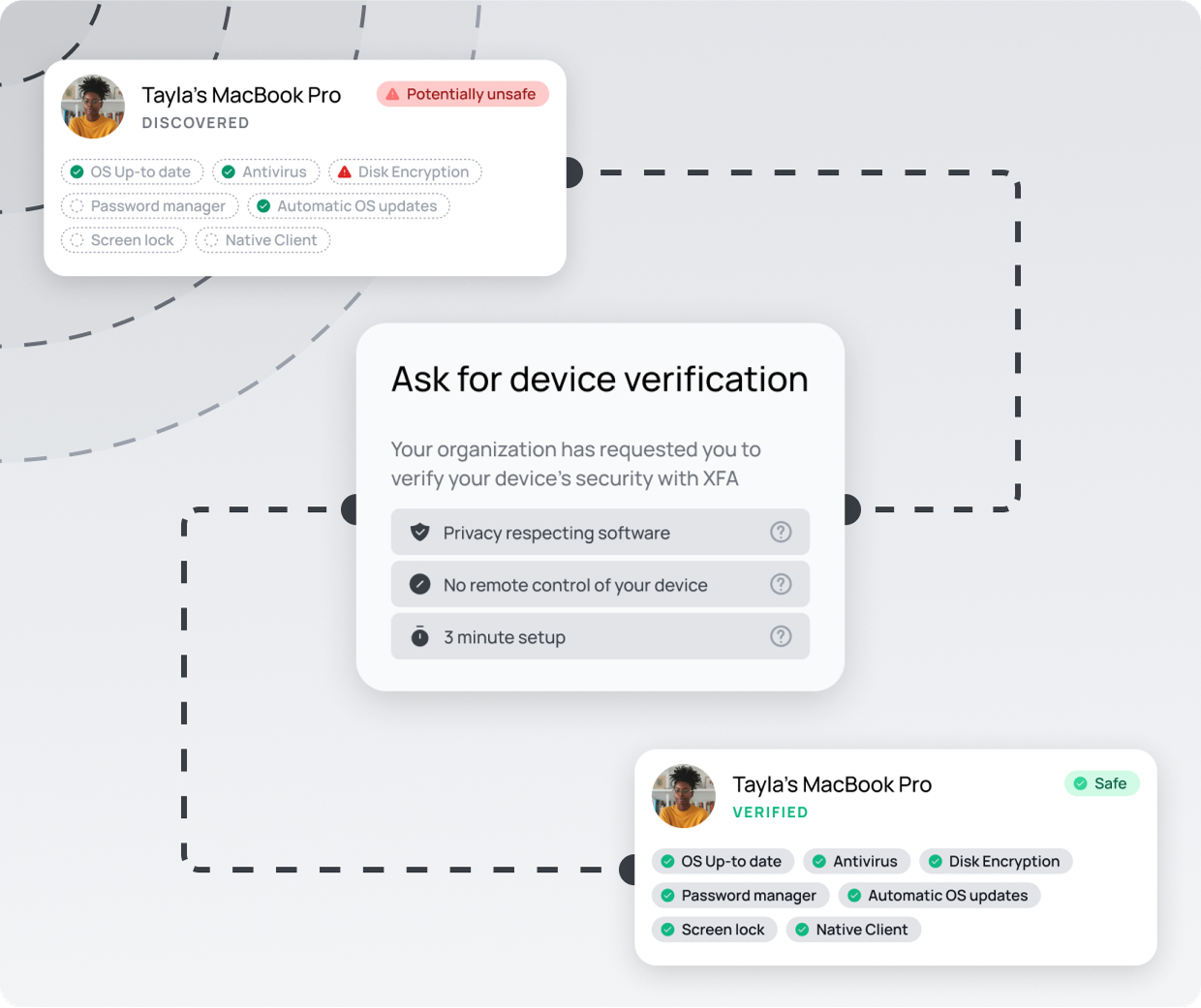
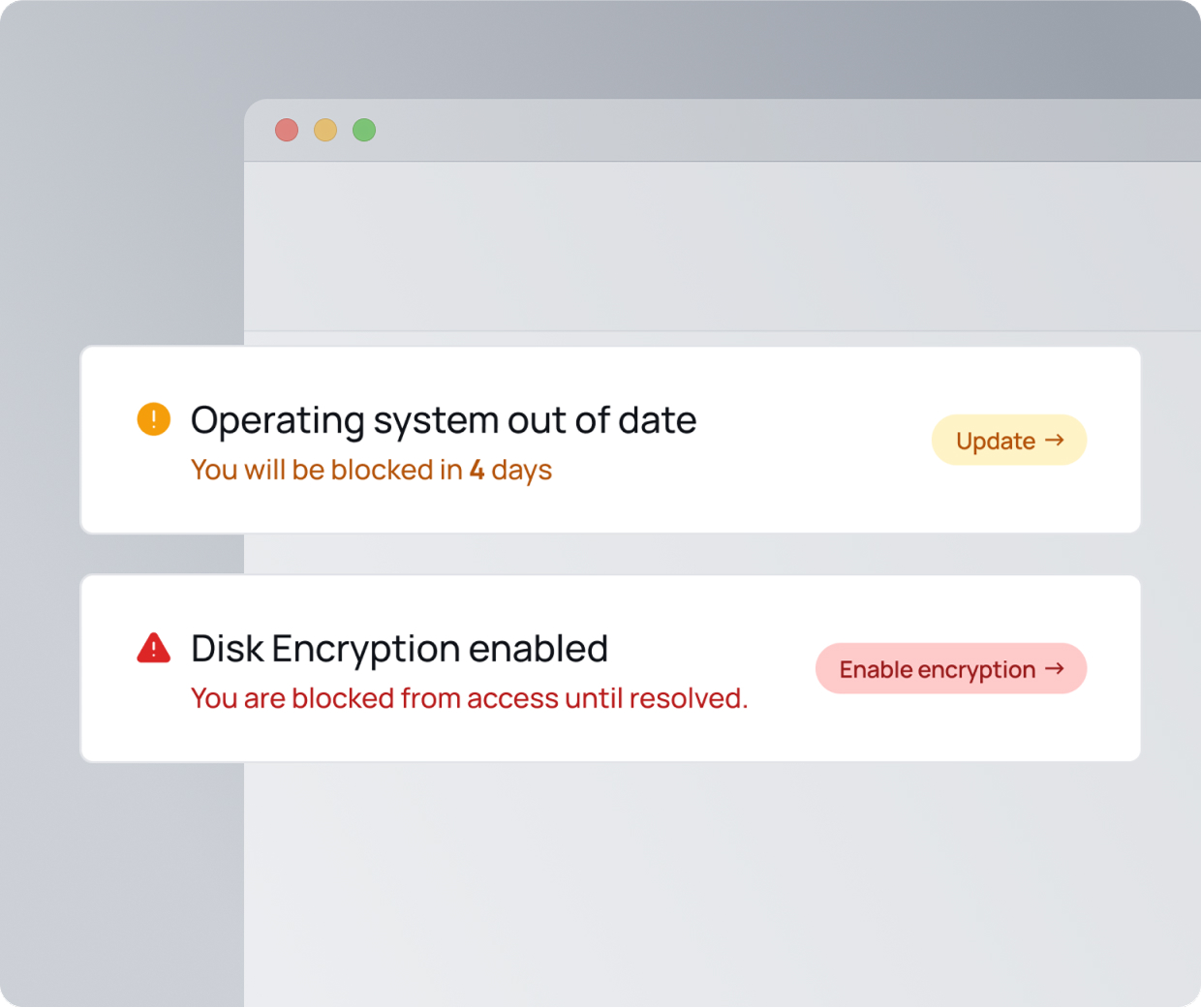
Security that guides.
So no one gets blocked.
Getting blocked slows work down. XFA gives users clear steps to fix security issues themselves, so they can regain access without IT intervention. Simple guidance, fewer disruptions, and a safer business.
XFA is crucial for us, as we rely on both managed and unmanaged devices. XFA's discovery phase helps us identify what devices are accessing sensitive information and ensures they comply with our security policies.
Your people are flexible.
Your security should be too.
Frictionless access, total security
Your team works anywhere with personal devices without risk. Freelancers and employees onboard easily, knowing their privacy is protected. No intrusive admin controls. Just a secure, productive team.
Only trusted devices get access
Every device is automatically verified before accessing systems. If a device becomes vulnerable, it's flagged and blocked. No breaches, no guesswork. Your business stays secure without IT overhead.
Compliance without the complexity
BYOD security isn't a challenge anymore. XFA keeps every device compliant without disrupting workflows. Your team stays productive and your business audit-ready without effort.
Want to secure all devices?
Let's talk.




