Enforce device security across your entire team
Ensure that only secure devices have access to your business data with XFA's comprehensive enforcement tools.
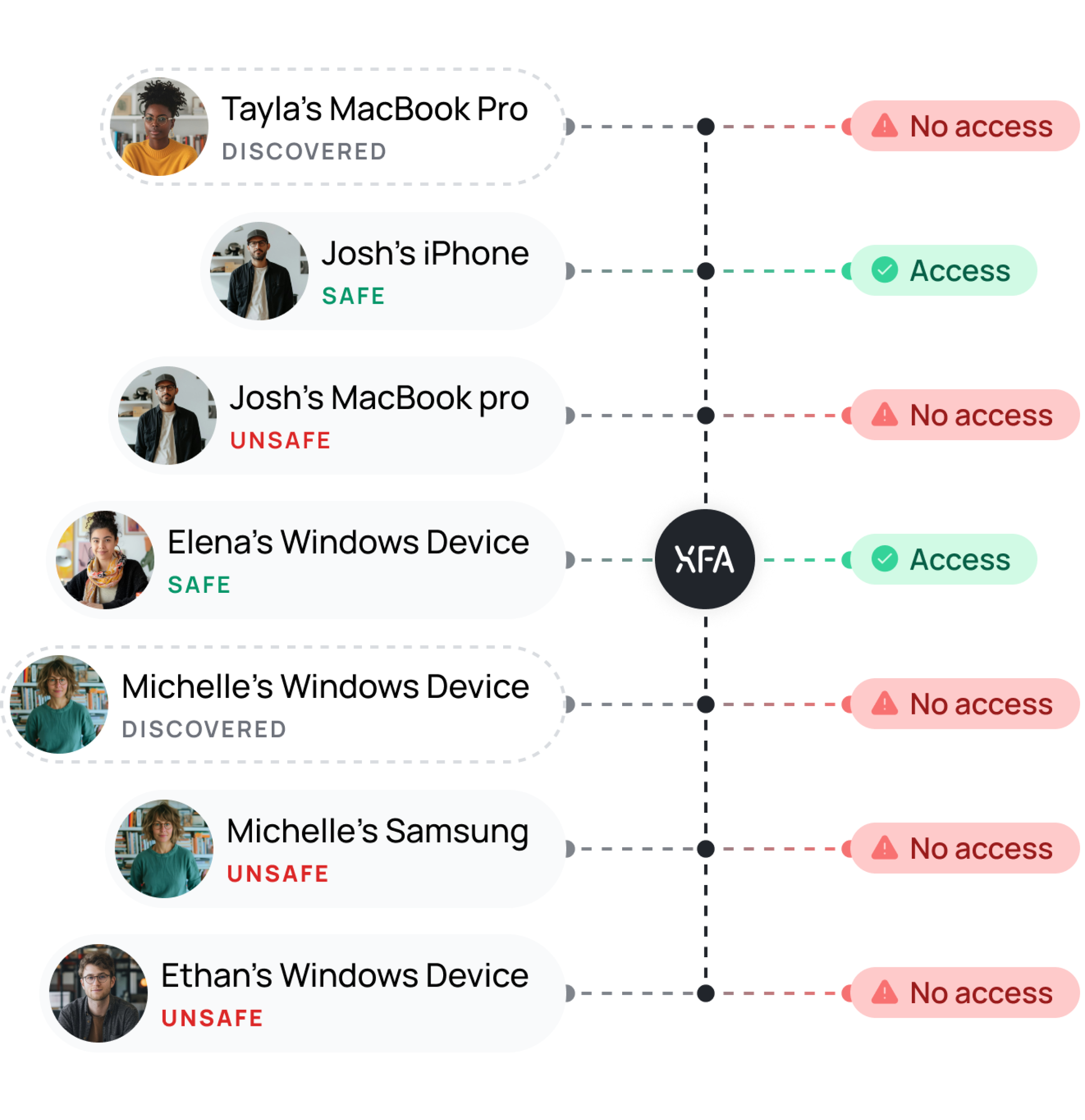
Protect sensitive data by enforcing secure access policies
In today's connected workplace, it's crucial that only trusted devices access your business data. XFA's enforcement feature automatically blocks unsafe devices, ensuring your security policies are consistently enforced.
Safeguard your data
Prevent unauthorized access with strict device security, protecting your data and ensuring compliance with framework like ISO27001, SOC2, NIS2, or DORA.
Streamline access control
Automate device access management, ensuring only compliant devices interact with your critical business systems.
Boost operational efficiency
XFA's automated enforcement eliminates manual checks, freeing your IT and security teams to focus on strategic initiatives rather than routine tasks.
Powerful tools for
comprehensive security enforcement
Covering all major identity providers
XFA integrates effortlessly with leading identity providers, fitting seamlessly into your company's existing software systems. Enhance your security across platforms without disrupting your workflow.
Microsoft 365
Integrate XFA into Microsoft Entra ID to ensure that only secure, compliant devices can access your Microsoft 365 environment.
Google Workspace
Connect XFA to Google Workspace, enforcing device security checks so that only verified, secure devices gain access to your organization's data.
Okta
Leverage Okta with XFA to manage identity while ensuring that only devices meeting your security standards can access critical applications.
OneLogin
Integrate XFA into OneLogin to enforce strict security policies, allowing only authenticated and secure devices to access your resources.
Ping Identity
Leverage XFA with Ping Identity to enforce device-level trust, ensuring only verified devices—assessed per your organization's security policy—can complete authentication.
SAMLv2 & OAuth2
Implement SAMLv2 and OAuth2 with XFA to provide secure, standards-based access, ensuring that only compliant devices are authorized.
Custom Integrations
Integrate XFA into your custom authentication mechanism to secure access across non-standard platforms, making sure only secure devices can connect.
Quick and easy self-onboarding for your team
Deploying enforcement across your team is quick and effortless. Once XFA is enabled, your team can complete the simple 3-minute setup themselves. The process is user-friendly, ensuring minimal disruption and quick adoption.
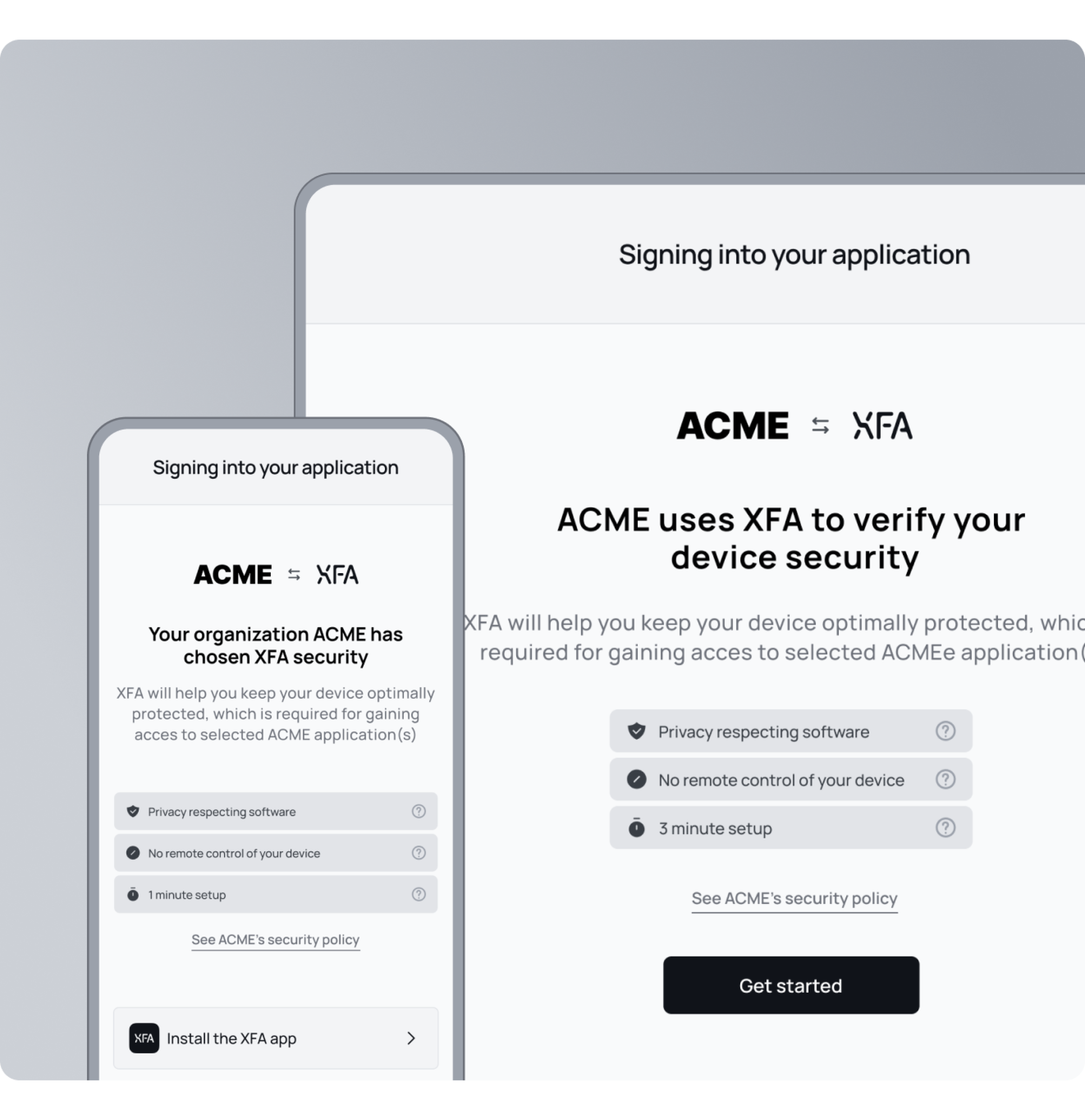
Create and enforce custom device policies easily
Develop device security policies within XFA that align with your organization's needs. Whether complying with ISO 27001 or SOC2, XFA ensures these policies are enforced across all devices, helping you stay compliant effortlessly.
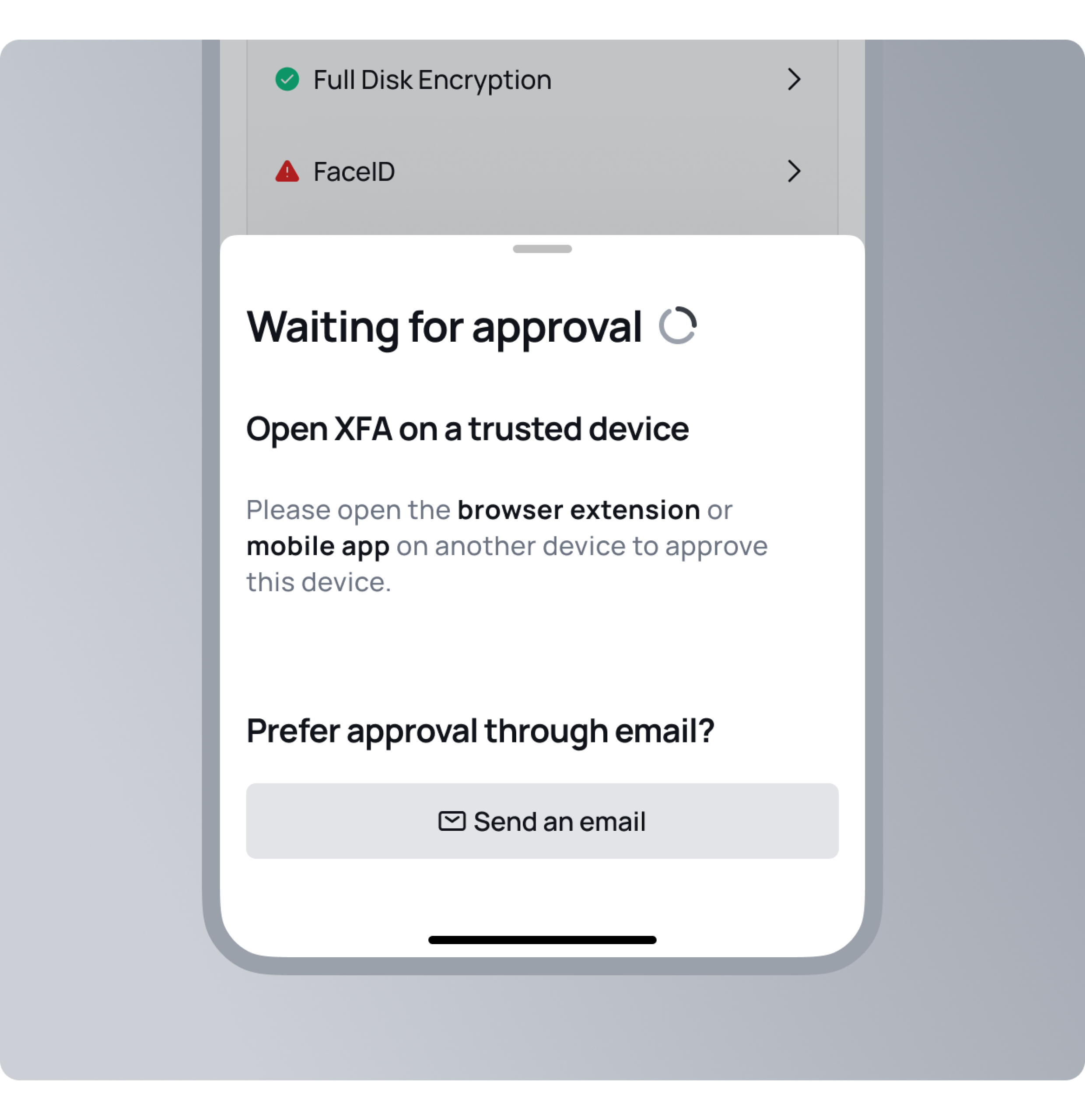
Simplified and secure multi-factor authentication
Enhance your security with (silent) multi-factor authentication integrated directly into your authorization process. XFA turns your devices into the authentication method, eliminating the need for codes or authenticator apps.
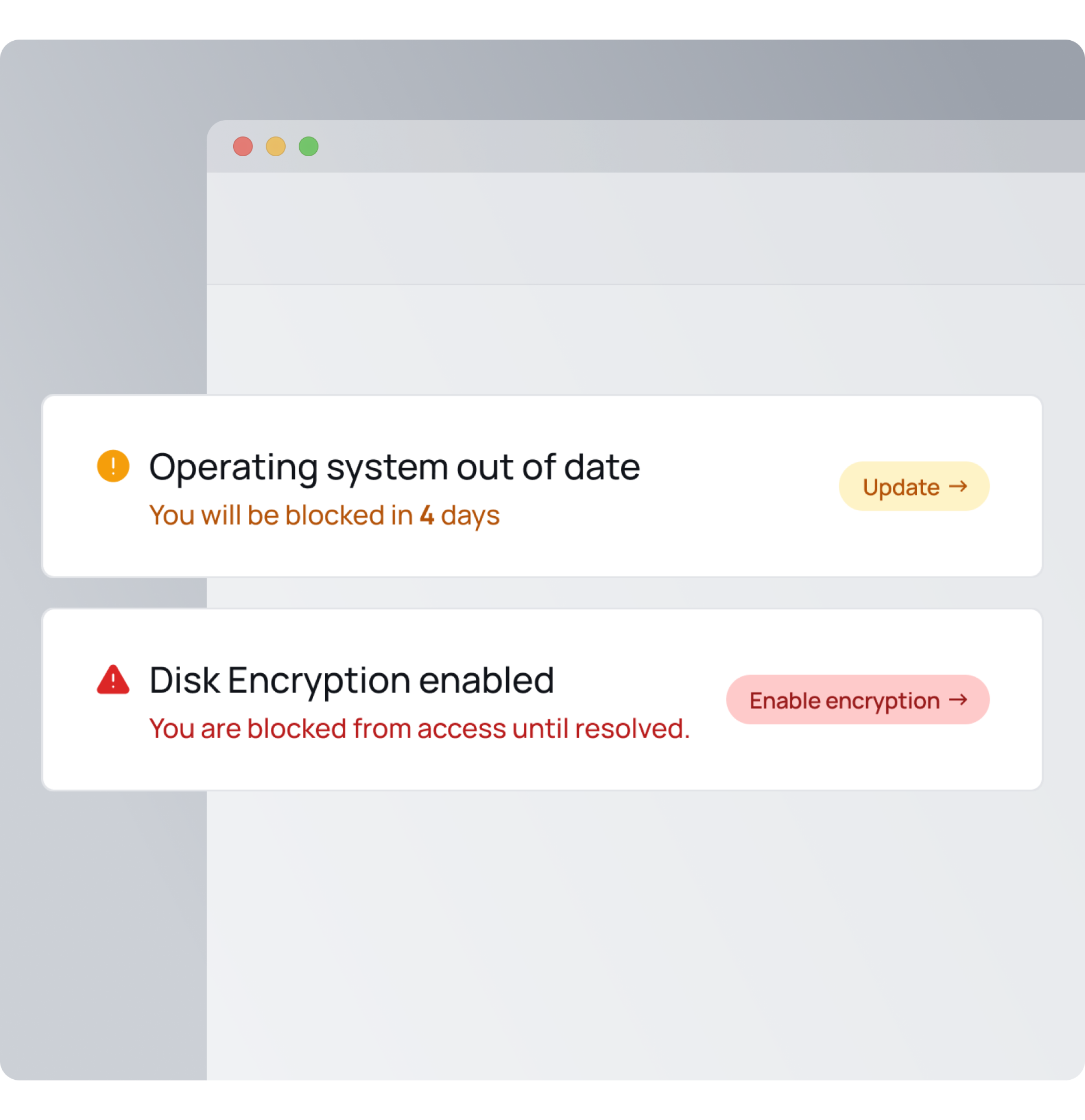
Keep access secure with XFA's device checks
XFA ensures only secure devices access your business applications by performing key security checks during authentication. By verifying measures like OS updates, encryption, and antivirus status, XFA reduces device-related risks and strengthens your overall security.
Quick self-onboarding and automated guidance simplify user management.
Every device accessing your systems will meet your security standards.
XFA proactively blocks unsafe devices, keeping your systems secure.

See how to secure your company with XFA's Enforcement feature
Watch our quick guide to see how to ensure that only secure devices have access to your business data
No time for a meeting?
Watch our solution video now.

We'd love to show you our solution and how:
- Every device is discovered automatically.
- Security is enforced without taking control or ownership of the device.
- Users can verify their devices from anywhere, in seconds.


