Agentless
No installation. No effort. No concerns.
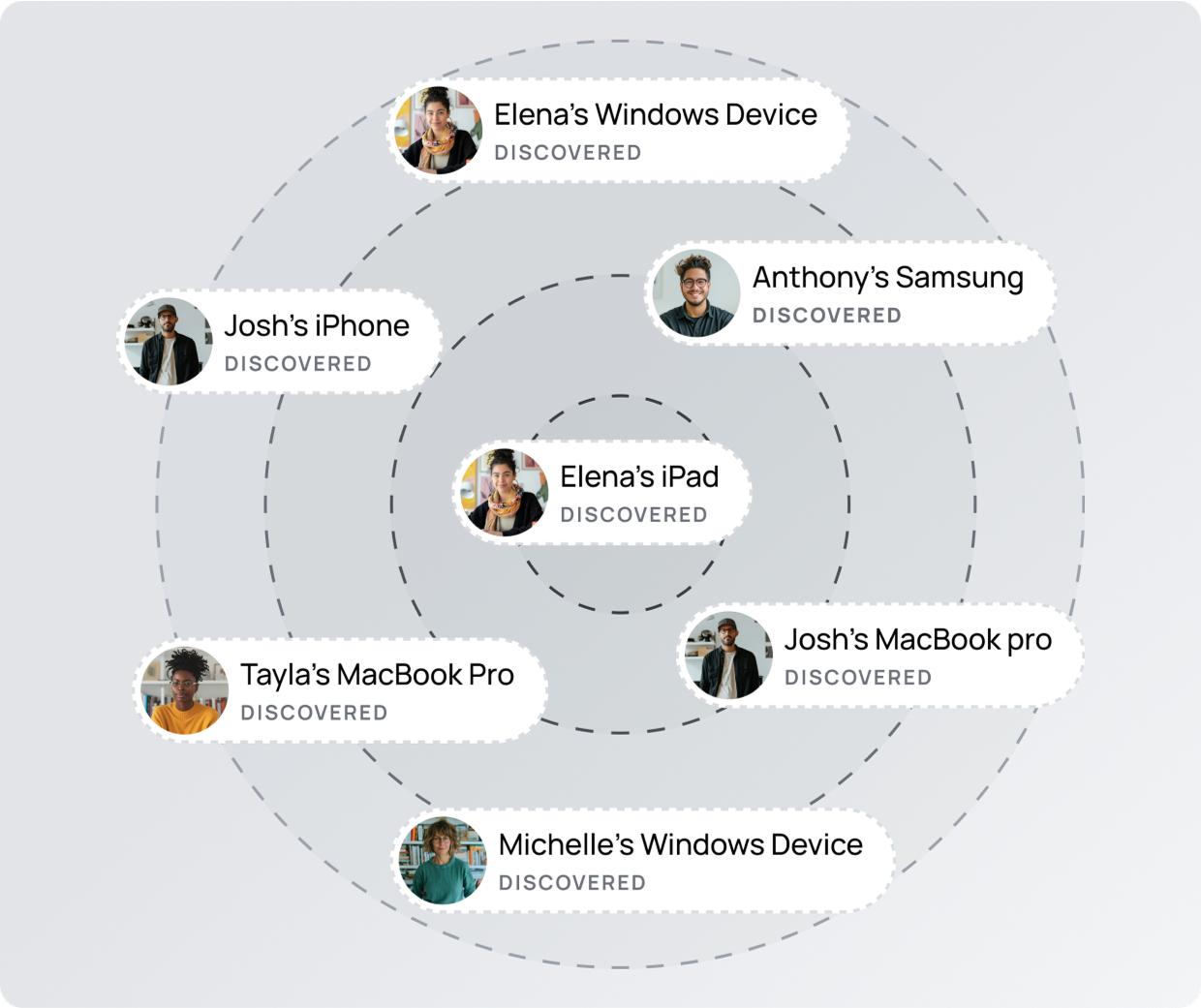
Agentless ensures every device can be included, secured, and compliant.
Nothing is left in the shadows.
Expand your device coverage.
Don't let friction leave devices in the shadows.
With XFA, organizations have already moved beyond the limits of traditional solutions. Our unique agent secures every device, anywhere, without invading privacy or taking control away.
But even small amounts of friction (agent installation, ownership questions, legal concerns) can slow adoption and leave devices out. Agentless removes those barriers, extending your security light to every device with zero effort from members of your workforce.
Zero installation
Verify device security instantly, without requiring an app or agent.
Full coverage
Expand coverage to all devices, including knowingly ignored ones, in the shadows.
No friction, no concerns
Secure devices without intruding on ownership, privacy, or legal concerns.
Agentless
No installation. No effort. No concerns.
Agentless ensures every device can be included, secured, and compliant.
Nothing is left in the shadows.
Expand your device coverage.
Don't let friction leave devices in the shadows.
With XFA, organizations have already moved beyond the limits of traditional solutions. Our unique agent secures every device, anywhere, without invading privacy or taking control away.
But even small amounts of friction (agent installation, ownership questions, legal concerns) can slow adoption and leave devices out. Agentless removes those barriers, extending your security light to every device with zero effort from members of your workforce.
Zero installation
Verify device security instantly, without requiring an app or agent.
Full coverage
Expand coverage to all devices, including knowingly ignored ones, in the shadows.
No friction, no concerns
Secure devices without intruding on ownership, privacy, or legal concerns.
See Agentless in action. Watch the launch film now.
Verify devices instantly.
No installation needed.
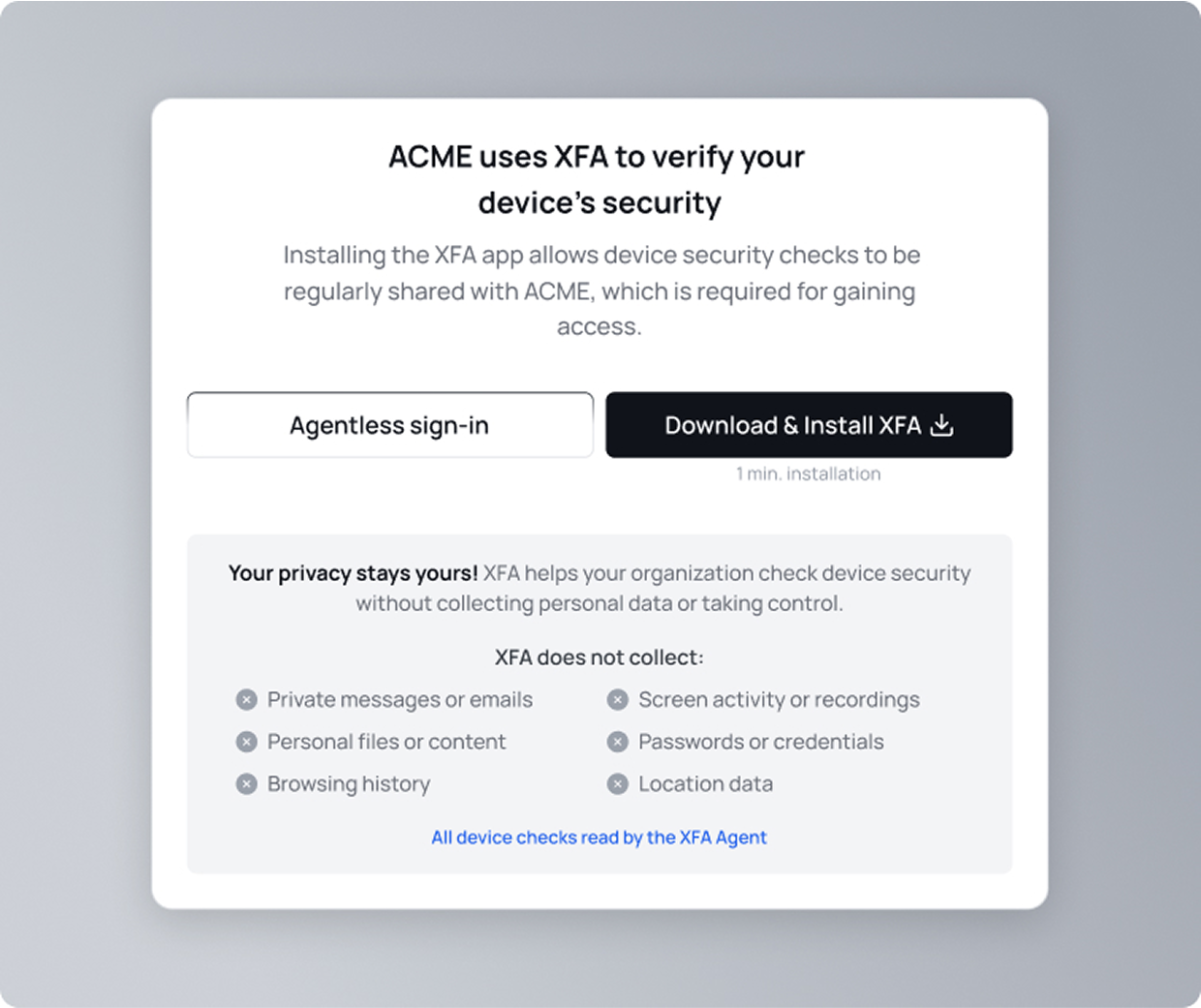
Agentless combines browser-based device signals with insights from XFA Discovery. This makes it possible to verify the security posture of a device and grant access using only the information already available.
Security without friction.
Agentless sign-in gets people straight to work, using the information that's already there. When changes are required, our personalized guidance still helps users fix issues quickly, without IT involvement.
And when teams want more, they can always upgrade to the full XFA agent for additional benefits.
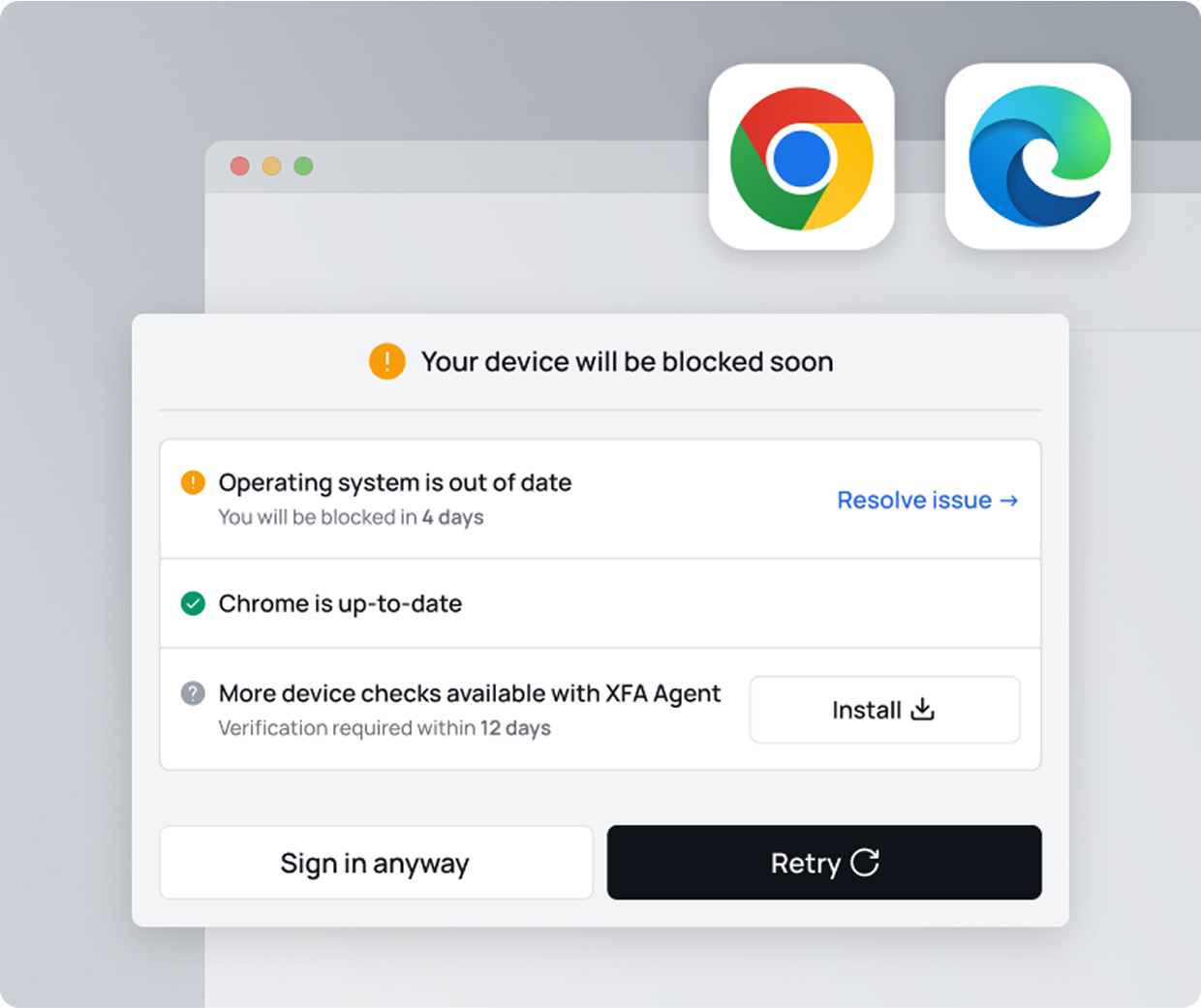
Critical checks, zero effort.
For mobile devices, Agentless already knows about the critical device checks every organizations wants to enforce — OS version, whether a passcode is set, and if a device is rooted or jailbroken.
For desktop devices, work profiles in browsers like Chrome or Edge share detailed security signals powered by our partners' new device trust features. Users don't need to install anything extra.
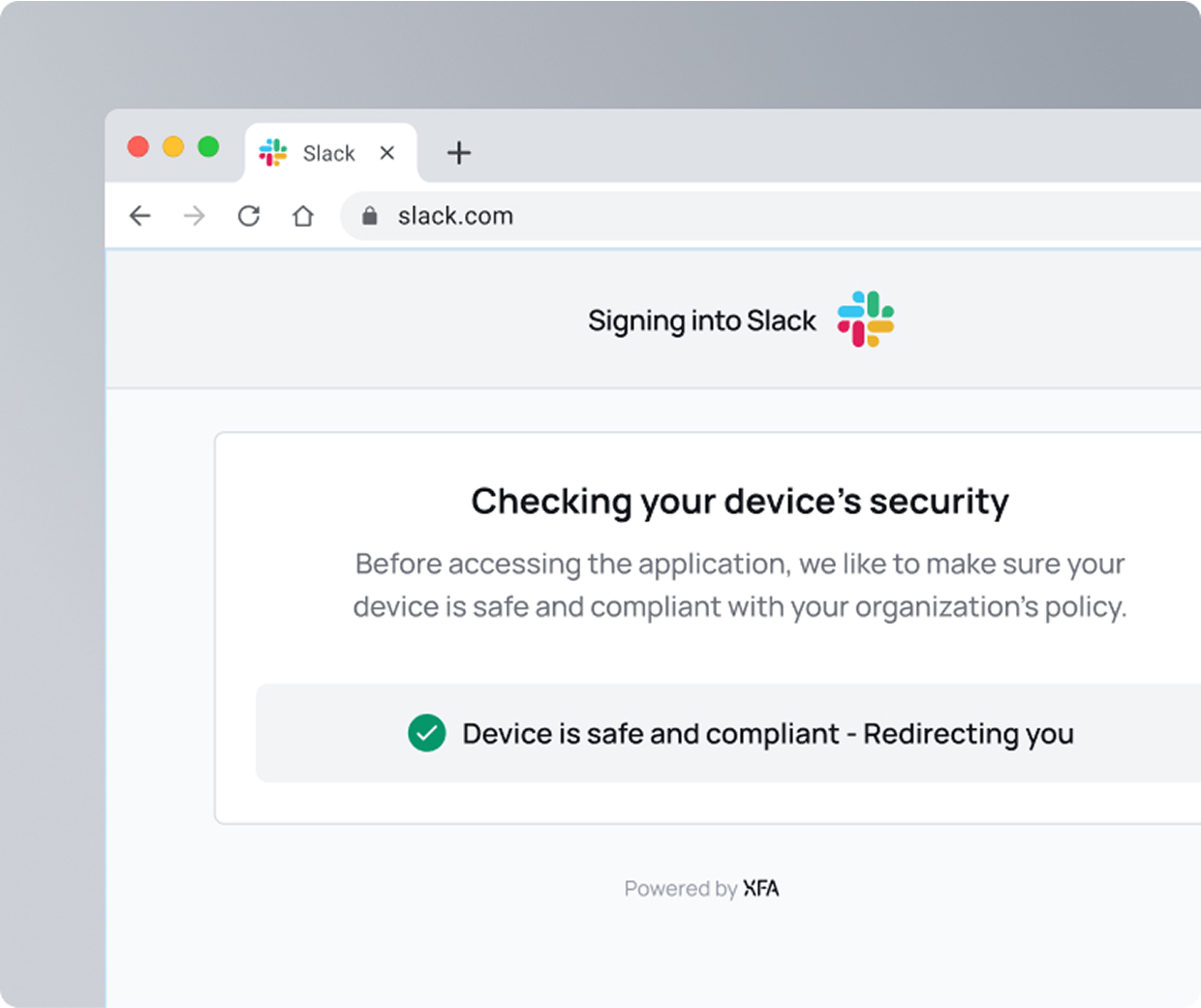
Your device security strategy without barriers.
Agentless lowers the effort across your entire device security strategy. Even in complex cases, where questions of ownership, privacy, or legal responsibility often create hesitation, Agentless removes those barriers.
Two powerful ways to secure every device.Choose the approach that fits your scenario.
Agentless
Agent
Agentless
No installation required. Devices can be verified instantly without apps or downloads.
Verifies device posture every time users access an application.
Expands coverage without effort. Makes it easier to include BYOD, contractors, and freelancers.
Agent
Lightweight install, effortless onboarding by end users everywhere, without trips to IT.
Provides continuous, in-depth security posture verification. Tracks device health over time.
Enables enforcement of advanced security policies – antimalware, screensharing, and other at scale.
Privacy-first: no access to personal data. Only posture information needed for compliance. Includes BYOD, freelancers, contractors, and other external parties.
Always the best user experience: with full user guidance and personalized step-by-step instructions, users know exactly what to do to fix issues quickly and confidently.
No time for a meeting?
Watch our solution video now.

We'd love to show you our solution and how:
- Every device is discovered automatically.
- Security is enforced without taking control or ownership of the device.
- Users can verify their devices from anywhere, in seconds.


