XFA — your privacy-respecting MDM alternative.
Protect your organization without having to take control or see into device trust, access control, and audit readiness.
Why MDM can't cover every device
BYOD and personal devices
Employees are often unwilling to install invasive MDM software on their personal laptops or phones, leaving security teams blind to risks introduced by unmanaged, yet connected, devices.
Contractors & freelancers
Temporary workers and partners may connect to your network using unmanaged devices. Without visibility or control, these endpoints become invisible risks that are difficult to track and prove trustworthy.
Third-party partners
Data breaches often originate from a third-party vendor's compromised device. MDM offers no visibility or monitoring, leaving your data exposed.
OS diversity
Many MDM solutions only support a limited set of OS. Some common examples include Linux, older operating systems, mobile devices, and more. This leaves large parts of your fleet unprotected.
Security that respects boundaries.
Protect every device, even the ones you don't manage.
XFA ensures you have visibility, enforcement, and reporting across every endpoint — managed or not.
Designed for hybrid teams, distributed work, and lean security operations.
Not bossware by design
XFA doesn’t scan content, track activity, or monitor usage. It only reads system-level signals needed to assess device posture — like encryption status or OS version.
Read-only, user-first
XFA never forces changes. Users stay in control and are guided to fix issues before being granted access — no device takeover, no surprise installs.
No admin required
No elevated permissions, no remote management tools, and no MDM profiles. XFA works instantly without IT overhead or user resistance.
Cover every endpoint.
Even those MDM can't see.
Freelancers, BYOD, and third parties should no longer be blind spots.XFA gives you full-fleet visibility. All across personal laptops, unmanaged desktops, BYOD, and contractor devices — ensuring that every endpoint meets your standards before it touches your systems.
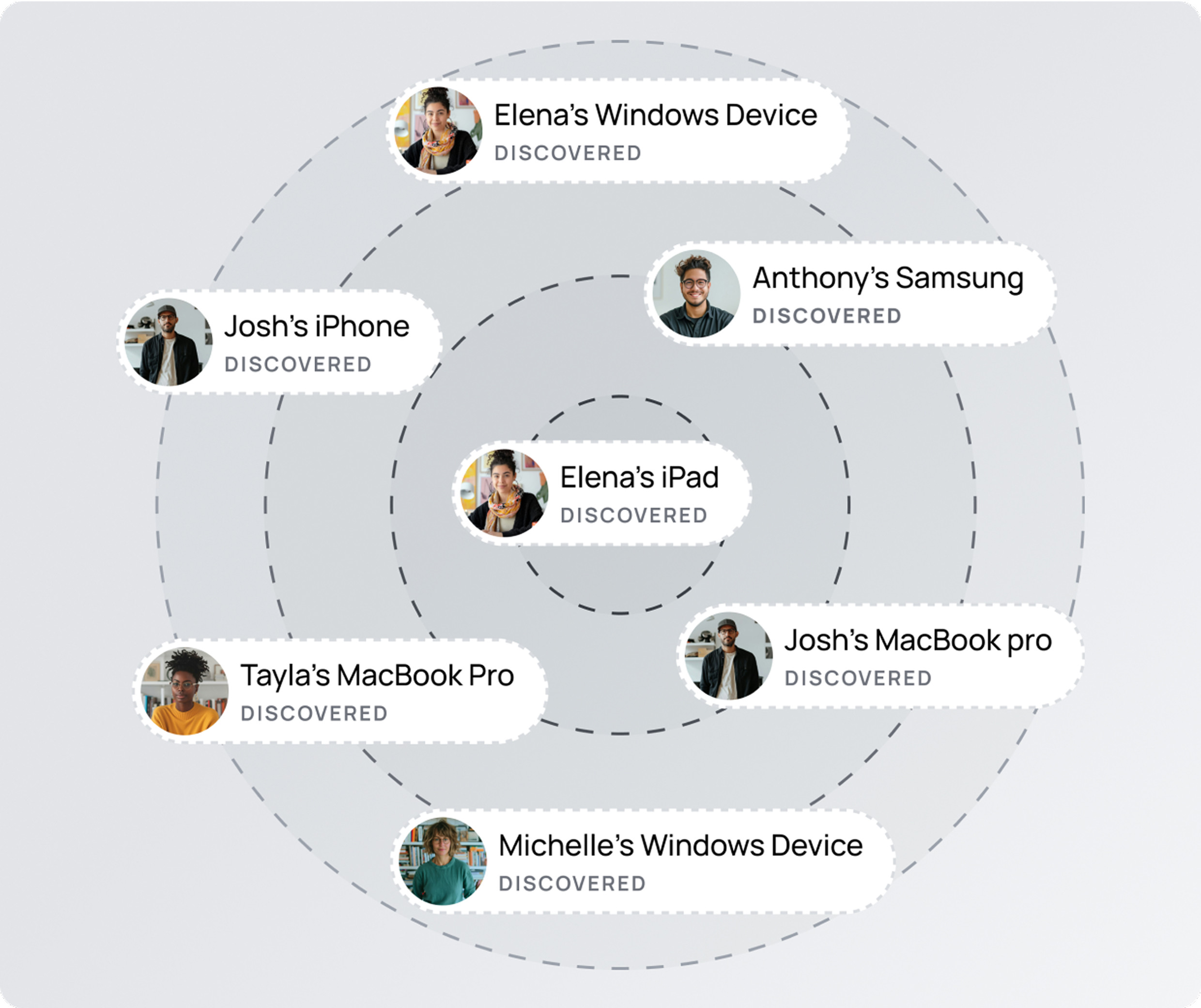
Respect privacy.
Still enforce security.
XFA guides users to resolve issues on their own, instead of having silent background controls or pushing risky overrides. No remote access, no hidden surveillance — just clear steps, visible posture checks, and a trusted path to secure access.
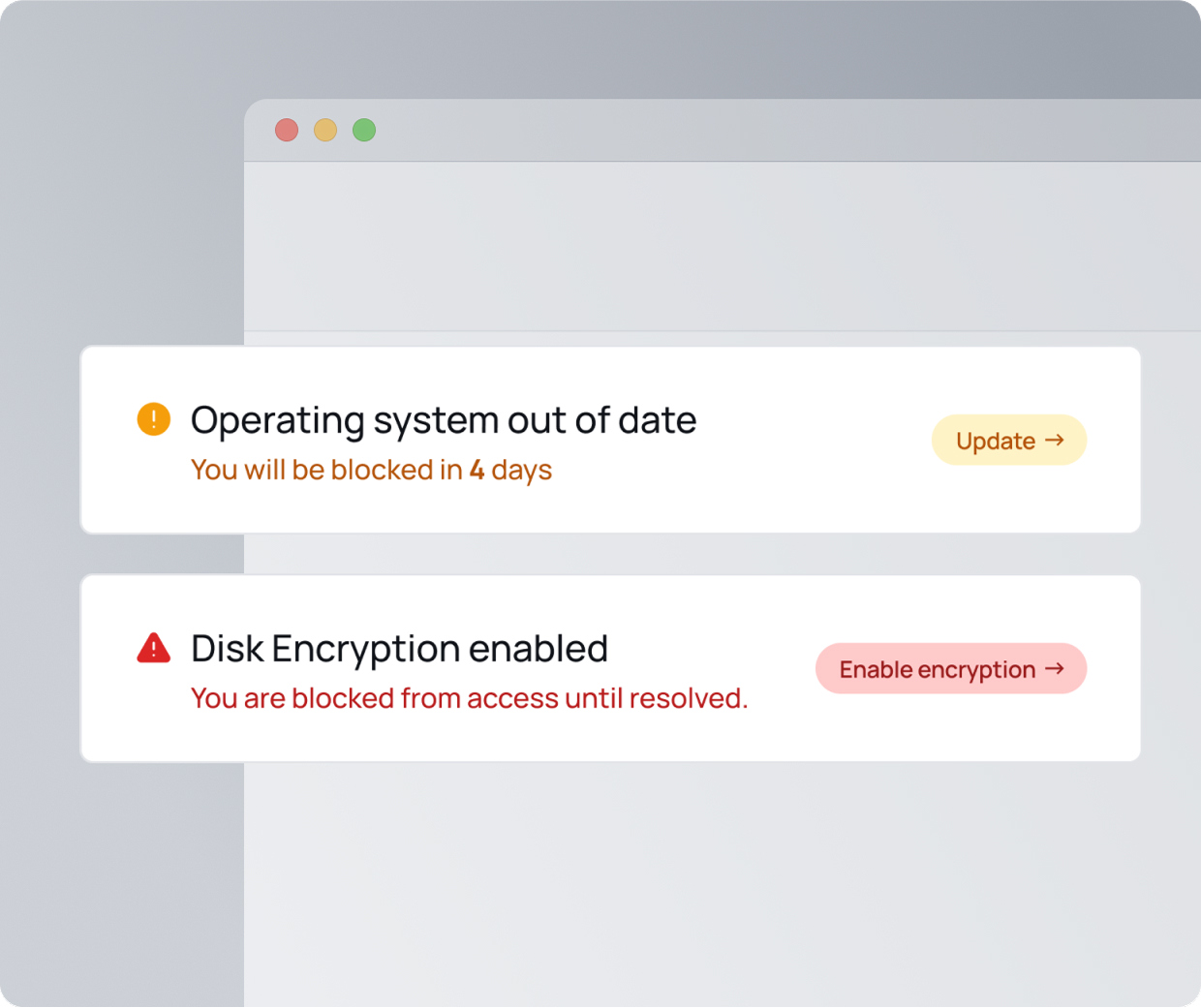
Secure access starts with smarter device checks
XFA verifies each device’s security posture (including OS updates, encryption, antivirus, and more) before granting access to your business apps. This ensures only trusted endpoints get through, reducing risk without slowing teams down.
Quick self-onboarding and automated guidance simplify user management.
Every device accessing your systems will meet your security standards.
XFA proactively blocks unsafe devices, keeping your systems secure.

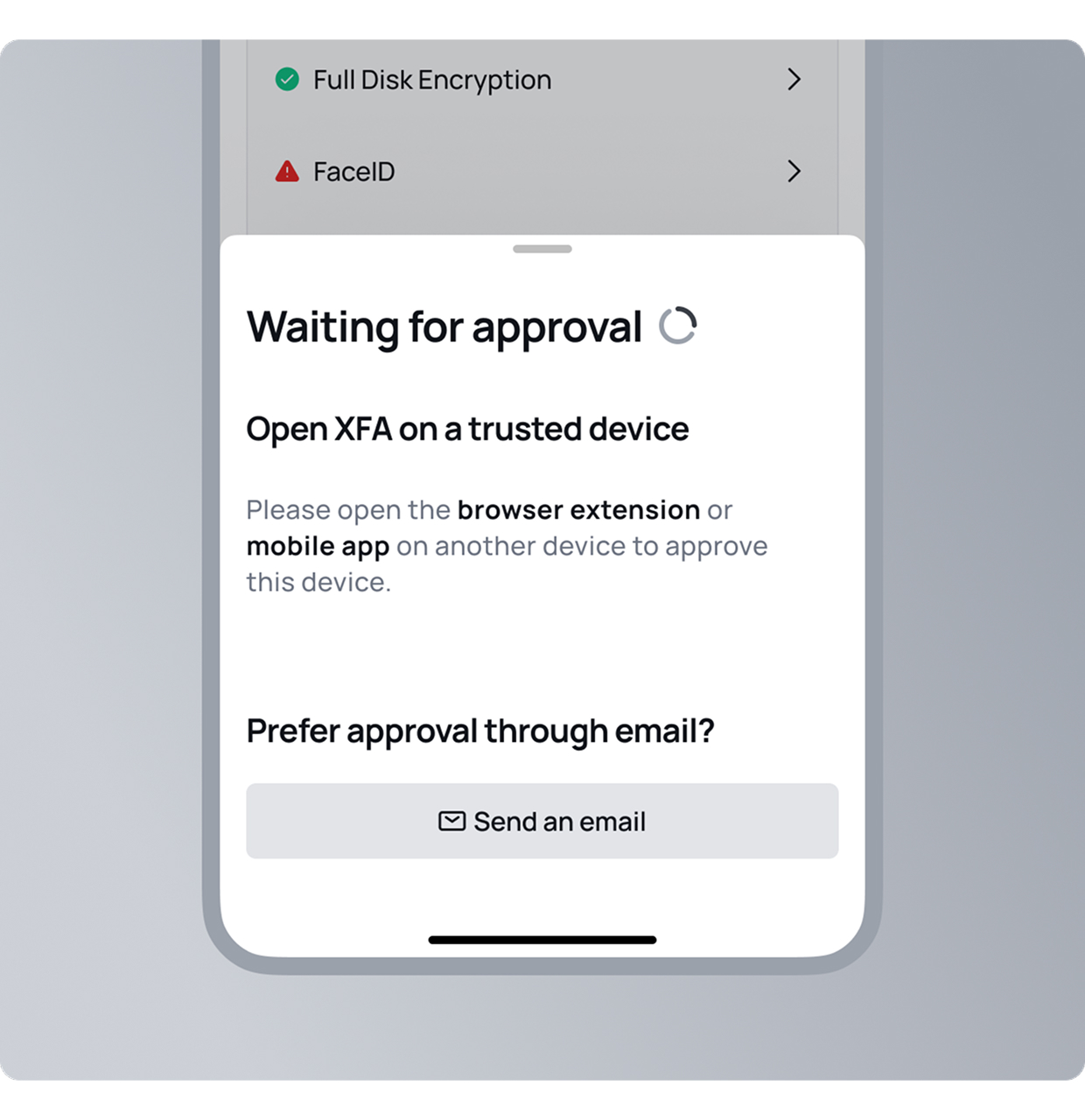
Easy and reliable multi-factor authentication
Strengthen security with seamless, silent multi-factor authentication built into your access workflow. With XFA, the device itself becomes the authentication factor, removing the need for passcodes or external authenticator apps.
What our customers say
No time for a meeting?
Watch our solution video now.

We'd love to show you our solution and how:
- Every device is discovered automatically.
- Security is enforced without taking control or ownership of the device.
- Users can verify their devices from anywhere, in seconds.




