XFA for Enterprise.
Cover device security gaps.
XFA helps large organizations fill critical visibility gaps in their device security strategy. XFA gives you instant clarity into what devices are connecting to your business platforms, without adding friction.

Enterprise teams often invest heavily in device management, but unmanaged, personal, BYOD devices still slip through. XFA adds real-time device visibility and enforcement at login to close that gap efficiently.
Challenges in enterprise today
How XFA helps reach full device visibility.
Modern device security that complements your stack.
XFA extends your enterprise device security with device policy enforcement at login. It fills the gaps that MDM tools miss, giving security and compliance teams full visibility into every device accessing critical systems.
Full device visibility beyond MDM
Discover unmanaged, BYOD, personal, and third-party devices that traditional tools overlook, all without taking away control of the device.
Policy enforcement at login
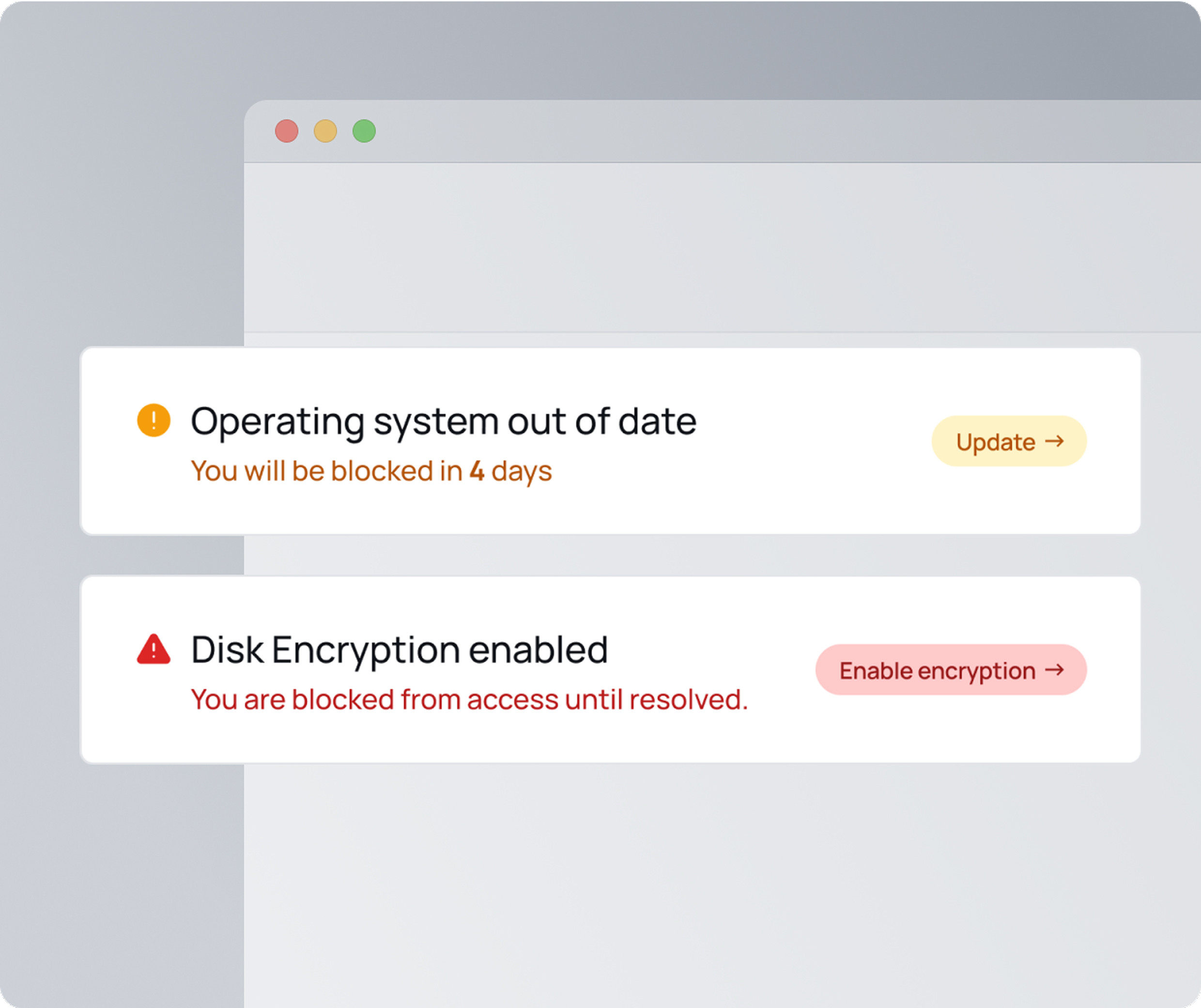
Automatically verify device posture before logins to your apps. Ensure disk encryption, OS updates, screen lock, and more, without invading privacy.
Privacy-respecting design
XFA runs silently in the background, respects user privacy, and eliminates friction, so that security doesn't slow work down.
Audit-ready compliance
Meet SOC 2, ISO 27001, and other frameworks needs with audit-ready evidence. No more manual spreadsheets.
Remote onboarding & instant access
Skip manual device setup. Onboard thousands of users fast and instantly, even freelancers and remote teams, with no IT tickets or heavy deployment.
Covering all major identity providers
XFA integrates with main identity providers, like Microsoft 365, Google, Okta, and more, fitting seamlessly into your existing software systems.
Secure every device, meet every standard.
Simplify enterprise compliance with real-time device evidence.
Enterprise audits demand real proof of enforcement. XFA gives security and compliance teams live visibility into every device accessing sensitive systems, whether it's managed, unmanaged, BYOD, or contractor-owned.
ISO 27001
A go-to framework for enterprises handling sensitive data or selling to enterprise buyers. XFA helps implement posture checks, enforce device standards, and prepare for audits faster.
Learn more →SOC 2 (Type 2)
See exactly which devices are accessing your environment and whether they meet your security baseline. XFA provides continuous device security evidence for auditors, without manual spreadsheets.
Learn more →NIST CSF
Strengthen every phase of the NIST CSF. XFA delivers real-time device discovery, posture monitoring, and access enforcement to support enterprise security programs.
Learn more →The power of device discovery
With just a few clicks, XFA identifies all devices accessing your platforms. No installs, just a fast, frictionless way to gain full visibility across employee, contractor, and partner devices. Click through and see how effortless securing your enterprise can be.


Secure access starts with smarter device checks
XFA verifies each device's security posture (including OS updates, encryption, screen lock, and more) before granting access to your tools. It adds a critical layer of device-based verification to your stack, so only secure, policy-compliant devices are let through.
Simple self-onboarding for new hires and contractors
Lightweight, user-friendly enforcement at login
Secure access across BYOD and distributed teams
Respect privacy while enforcing security
Your workforce is diverse. Employees, contractors, and third parties often use their own devices. But that shouldn't mean compromising on device security. XFA checks device posture without invading privacy or taking control, helping you meet compliance requirements.
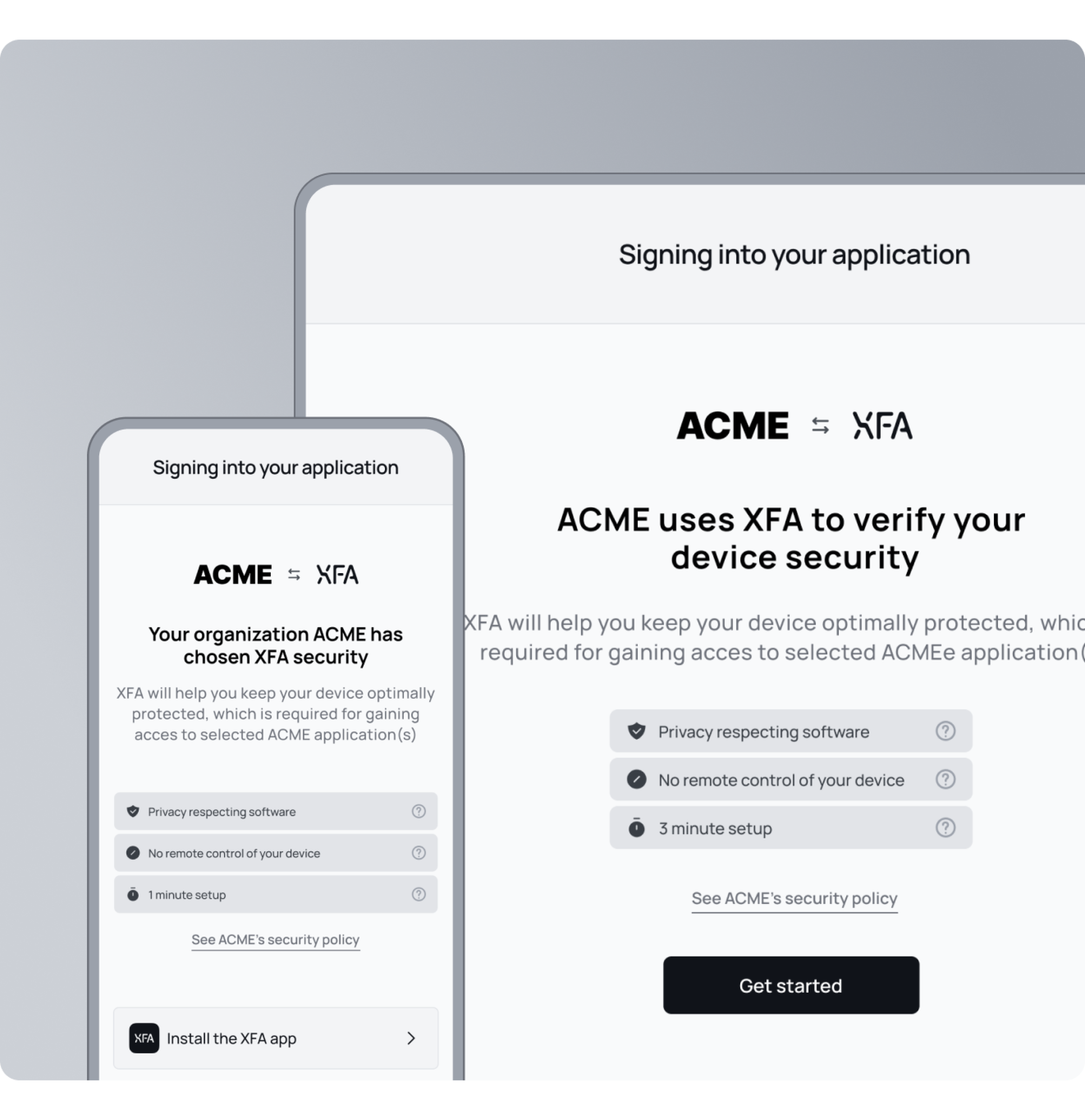
Quick and easy onboarding for new hires
New joiners, freelancers, or temporary staff? XFA gets them onboarded securely in minutes, without IT overhead. A simple 3-minute setup ensures every device meets your security requirements from day one, so your team can always stay productive.
No time for a meeting?
Watch our solution video now.

We'd love to show you our solution and how:
- Every device is discovered automatically.
- Security is enforced without taking control or ownership of the device.
- Users can verify their devices from anywhere, in seconds.






