XFA for Healthcare.
Protect every device.
Secure patient data, protect clinical workflows, and stay compliant, even with BYOD and remote teams. XFA helps healthcare tech providers meet global device security standards without slowing down care.

The healthcare and medtech sector is rapidly evolving, but security practices often lag behind. With sensitive health data, strict regulations, and a distributed workforce, staying secure and compliant across every device is harder than ever.
Challenges in healthcare today
How XFA protects healthcare workflows.
Features built for modern health systems.
XFA gives healthcare organizations real-time visibility and access control across all devices without requiring full control or complex setup. It's security that matches how modern care teams actually work.
Real-time device visibility
Automatically detect every device connecting to your systems, whether it's a nurse's BYOD tablet, a contractor's laptop, or a remote employee's desktop.
Enforcement of smart access policies
Verify device posture (OS version, encryption, etc.) before granting access to sensitive platforms, without full device control or MDM enrollment.
Privacy-respecting design
Protect sensitive medical data without tracking or collecting personal info from users' devices. Staff information stay private, devices stay secure.
Audit-ready compliance
XFA generates continuous, exportable compliance evidence for audits like ISO 27001, NIS2, HIPAA, and GDPR, replacing manual audit spreadsheets.
Remote onboarding & instant access
Onboard clinical or support staff from anywhere, in minutes, even on their own devices, with a simple 3-minute setup.
Covering all major identity providers
XFA integrates with main identity providers, like Microsoft 365, Google, Okta, and more, fitting seamlessly into your existing software systems.
Secure every device, meet every standard.
Simplify compliance without disrupting care delivery.
XFA helps you meet critical healthcare data protection standards. Automated posture checks and audit-ready evidence make compliance easier, even in dynamic, distributed environments.
ISO 27001
The standard for information security management, especially for healthtech providers handling PHI. XFA supports ISO 27001 by automating posture verification and enforcing policy at the point of access without compromising usability.
Learn more →NIS2 (EU)
As the EU expands its regulatory scope for critical sectors like healthcare, NIS2 demands stronger technical controls and risk mitigation. XFA verifies endpoint security, enforcing secure access without friction or taking away control.
Learn more →HIPAA (U.S.)
Essential for healthcare organizations and digital health companies handling electronic PHI. By verifying device posture at the point of access, XFA enables secure access while minimizing friction.
Learn more →The power of device discovery
With just a few clicks, XFA identifies all devices accessing your platforms. No installs, just a fast, frictionless way to gain full visibility across clinical staff, contractors, and third-party devices. Click through and see how effortless securing your healthcare organization can be.


Secure healthcare access with smarter device checks
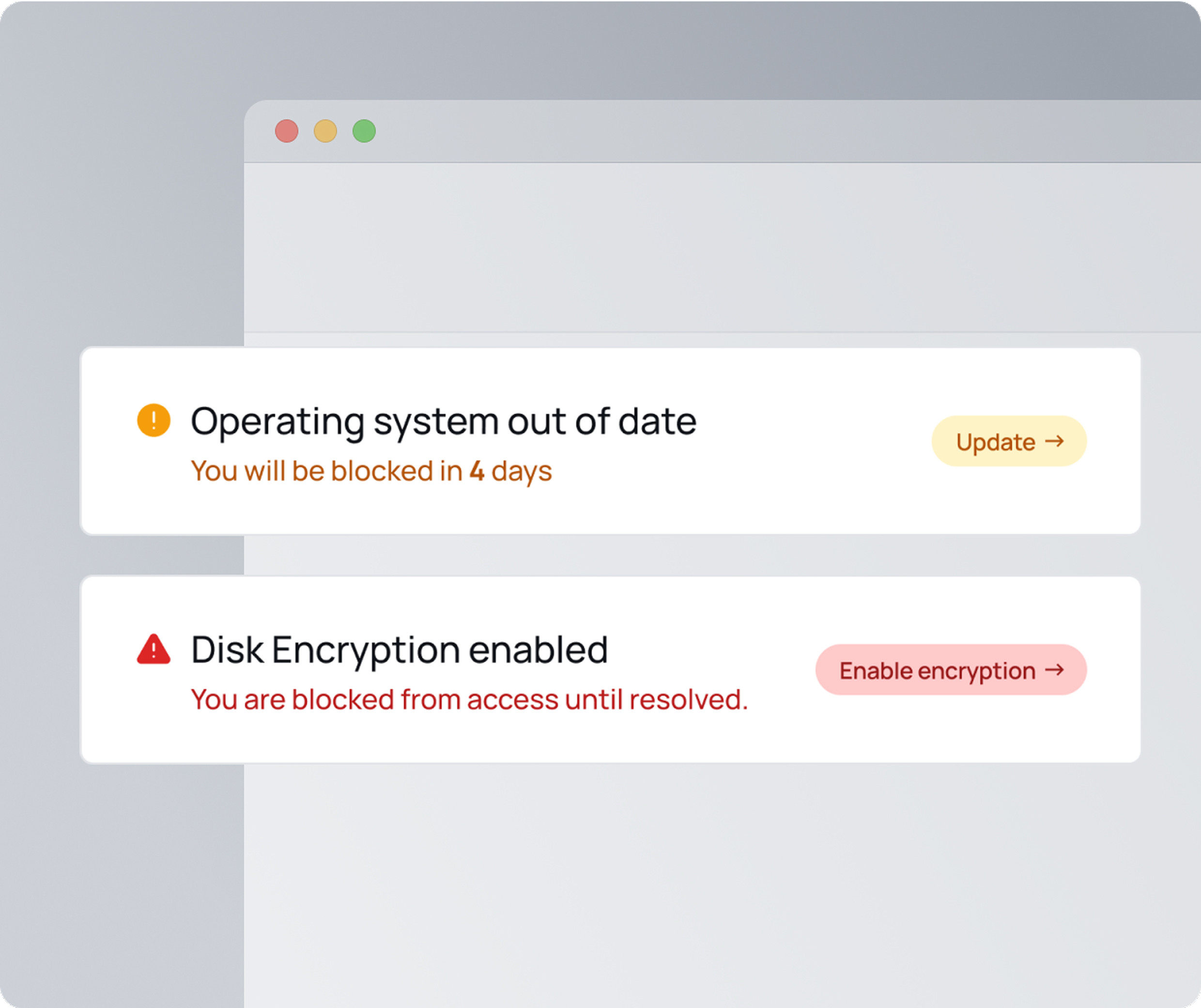
XFA verifies each device's security posture (including OS updates, encryption, screen lock, and more) before granting access to your platforms, care coordination tools, or internal apps. That means only compliant devices can access.
Remote, easy self-onboarding for new hires
Lightweight, user-friendly enforcement at login
Secure access for every employee, no matter the device
Respect privacy while enforcing security
No hidden control, no intrusive software. XFA gives clinicians, staff, and external partners clear, respectful guidance to resolve device issues, without surveillance or IT overhead.
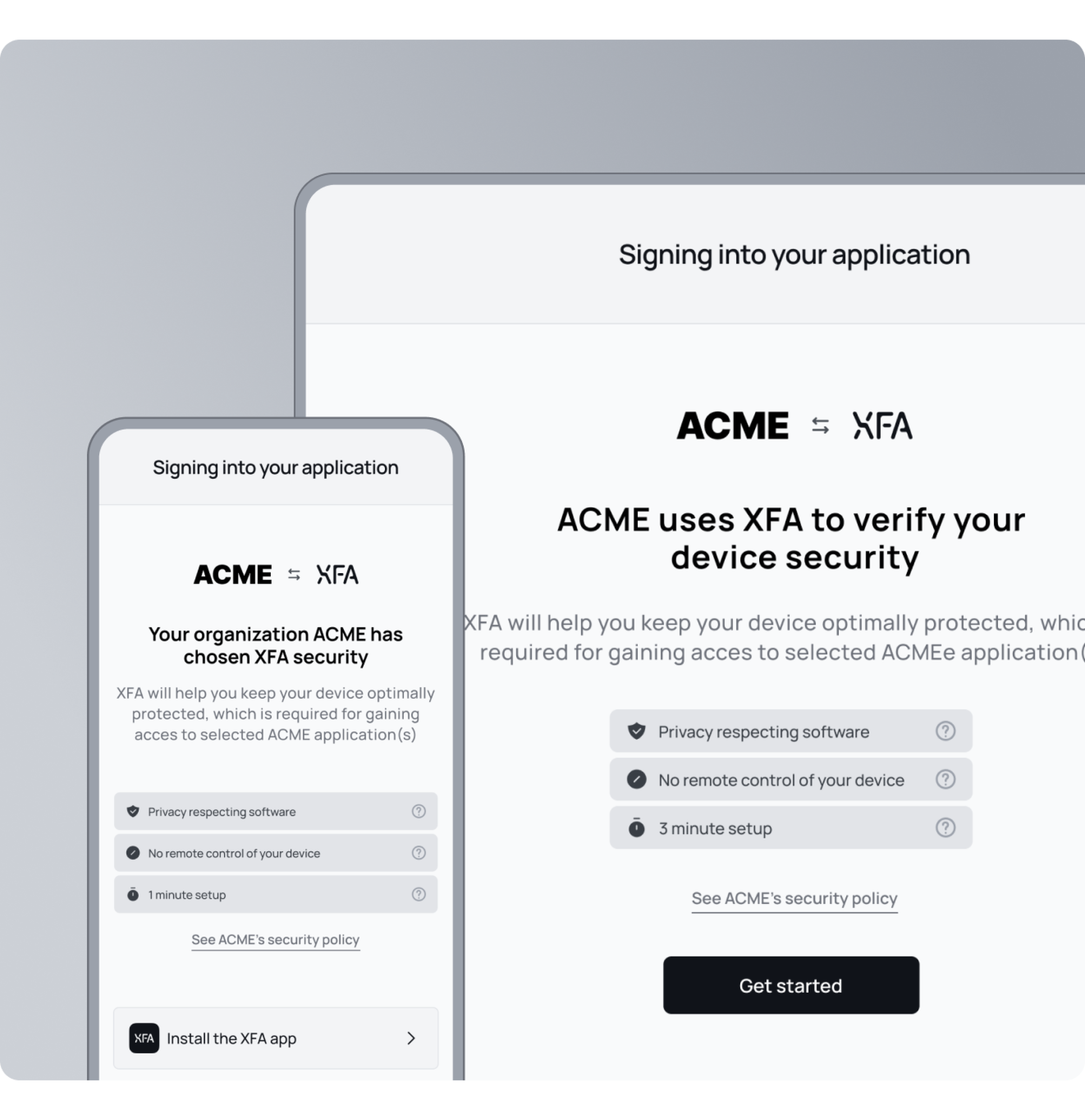
Quick self-onboarding for all clinical staff
From doctors working remotely to traveling nurses and admins, XFA enables secure access in minutes. No shipping, no MDM enrolment, just a simple 1-minute setup from any device, anywhere in the world.
No time for a meeting?
Watch our solution video now.

We'd love to show you our solution and how:
- Every device is discovered automatically.
- Security is enforced without taking control or ownership of the device.
- Users can verify their devices from anywhere, in seconds.






