XFA for Technology.
Secure innovation at scale.
Today's tech teams move fast: building, deploying, and collaborating across cloud platforms in hybrid teams. XFA helps secure every device accessing your systems, without slowing down development or delivery.

From remote dev teams to fast-moving SaaS environments, security and compliance can't be an afterthought. But traditional device management tools can't keep up.
Challenges in tech today
How XFA secures modern tech teams.
Features built for scaling organizations.
XFA brings scalable, privacy-respecting enforcement to hybrid, remote, and BYOD environments, which is ideal for software teams, product organizations, and IT leaders in fast-moving tech companies.
See every device instantly
Discover all devices connecting to dev tools, dashboards, internal systems. Whether it is managed, personal, or contractor-owned device.
Enforcement of smart access policies
Control access to business platforms: GitHub, Jira, cloud consoles and more, based on device posture. No MDMs or full device control needed.
Privacy-respecting design
XFA never monitors personal activity or collects sensitive data. Teams retain control of their devices without compromising access.
Audit-ready compliance
XFA generates continuous, exportable compliance evidence for audits like ISO 27001, SOC2, DORA, and NIS2, replacing manual audit spreadsheets.
Remote onboarding & instant access
New hires and freelancers can meet your security standards immediately and start building in minutes. There's no hardware shipping or MDM enrolment required. No overhead - keep productivity and optimize freedom.
Covering all major identity providers
XFA integrates with main identity providers, like Microsoft 365, Google, Okta, and more, fitting seamlessly into your existing software systems.
Secure every device, meet every standard.
Simplify compliance without slowing down teams.
From scaling product teams to onboarding remote engineers, tech companies are under pressure to stay secure and audit-ready. XFA helps meet leading compliance frameworks with real-time device checks and enforcement at login, not just paper policies.
ISO 27001
The leading international framework for information security management, trusted by tech companies worldwide. XFA helps implement and automate key checks like device posture checks and access policies.
Learn more →SOC 2 (Type 2)
Crucial for SaaS and B2B software providers looking to build customer trust and scale with confidence. XFA gives continuous, verifiable proof of device and access security, without deploying heavy tooling or relying on manual tracking.
Learn more →GDPR (EU)
For European and global companies, XFA enforces device-level access security without collecting personal or intrusive data. By verifying device posture at the point of access, XFA enables secure access while maintaining privacy.
Learn more →The power of device discovery
With just a few clicks, XFA identifies all devices accessing your platforms. No installs, just a fast, frictionless way to gain full visibility across employee, contractor, and third-party devices. Click through and see how effortless securing your tech team can be.


Secure engineering starts with smarter device checks
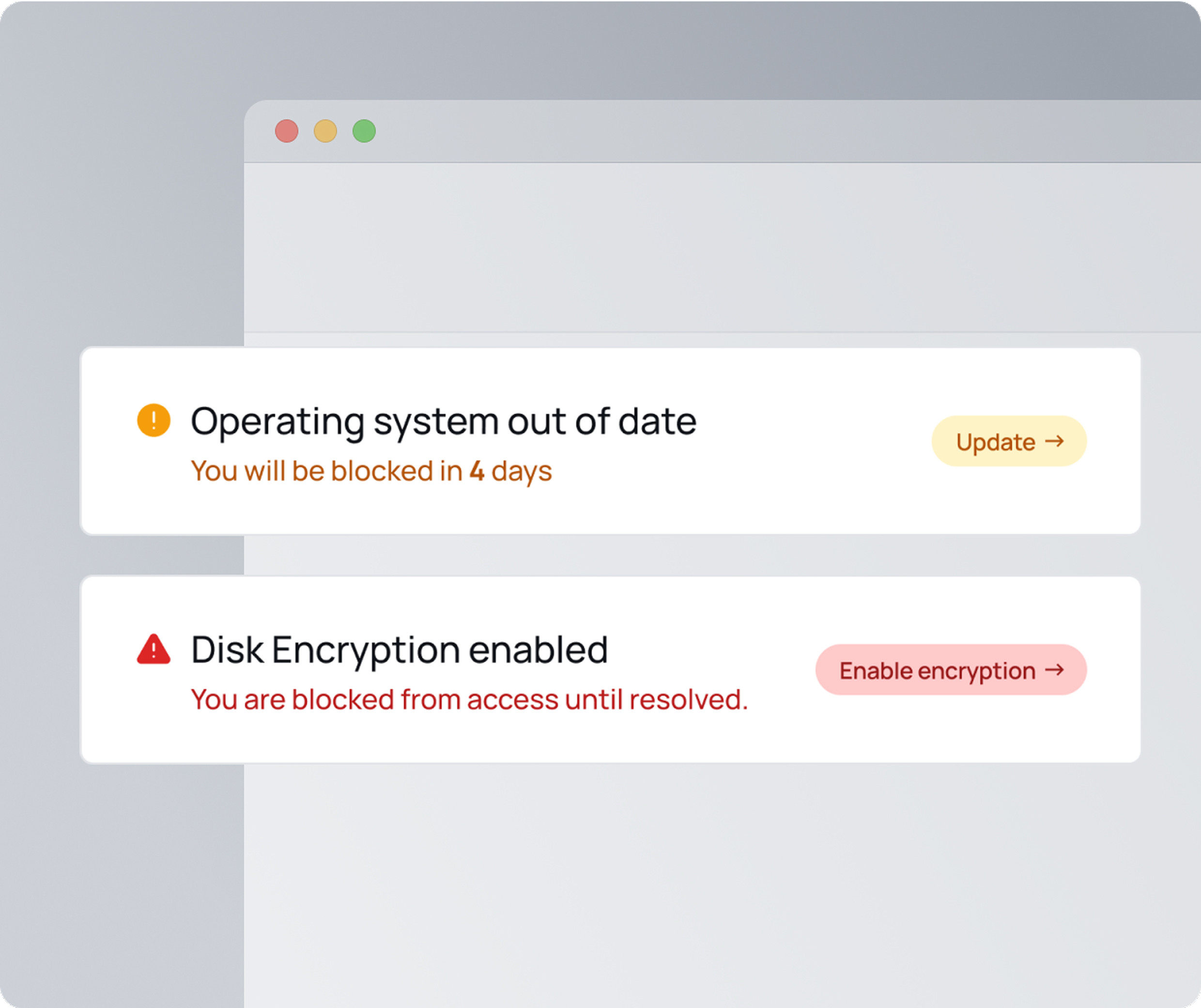
XFA verifies each device's security posture (including OS updates, encryption, screen lock, and more) before granting access to your business platforms. That means only compliant devices can access, letting fast-moving teams stay productive without skipping security.
Remote, easy self-onboarding for new hires, freelancers, and contractors
Lightweight, user-friendly enforcement at login
Secure access for every developer, no matter the device
Respect privacy while enforcing security
Your developers and contractors don't want MDMs watching their devices. XFA guides users to self-resolve issues and only checks what's necessary. No surveillance, no remote control, just real-time posture checks and clear enforcement.
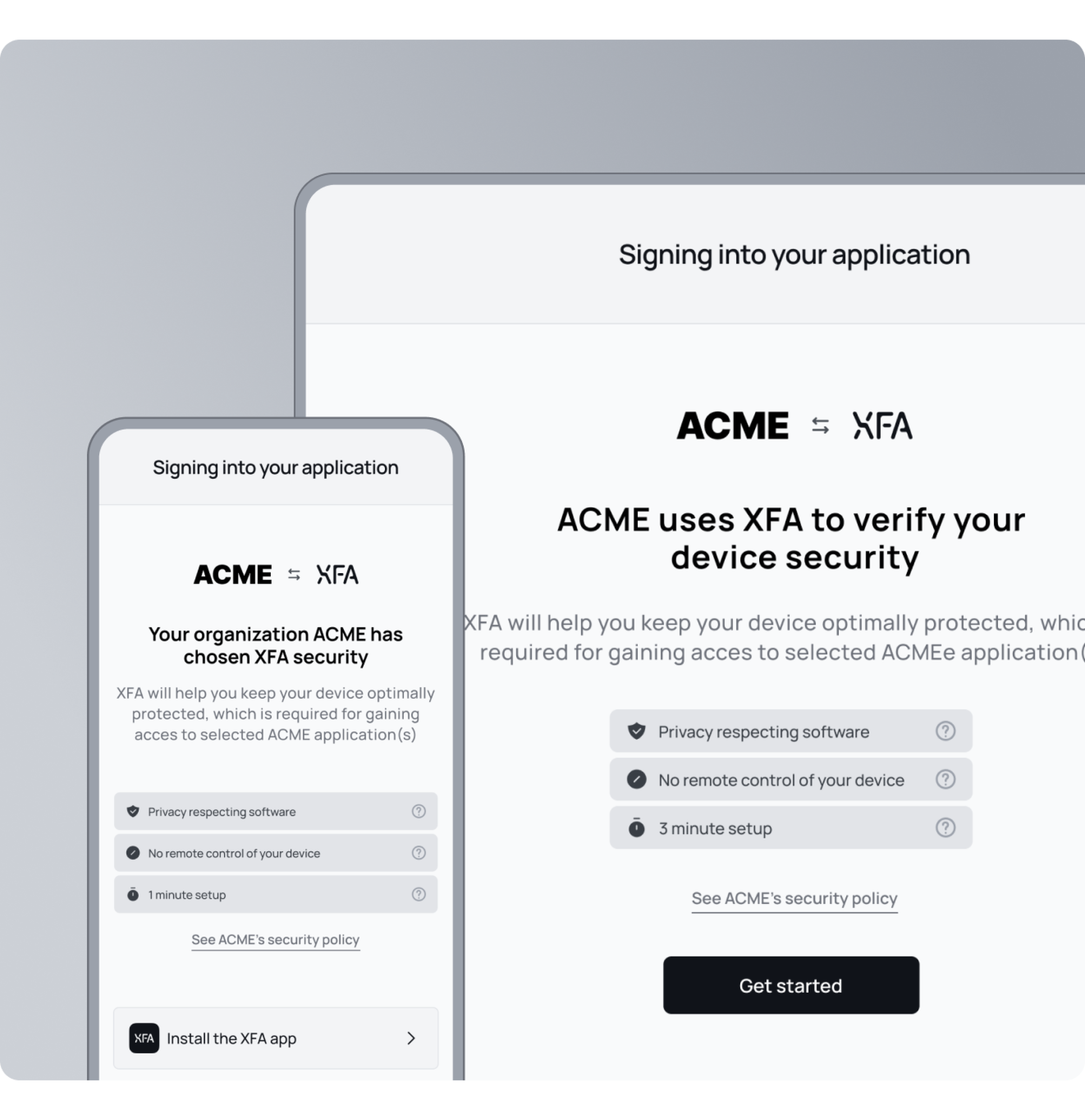
Quick self-onboarding for everybody
New team members can get started by completing a simple 1-minute setup on their own, from anywhere, on any device. XFA's lightweight setup ensures secure access on day one, with no need for IT overhead or device takeovers.
No time for a meeting?
Watch our solution video now.

We'd love to show you our solution and how:
- Every device is discovered automatically.
- Security is enforced without taking control or ownership of the device.
- Users can verify their devices from anywhere, in seconds.






